Operating system: Windows, Android, macOS
Group of programs: Business automation
Visitor control
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
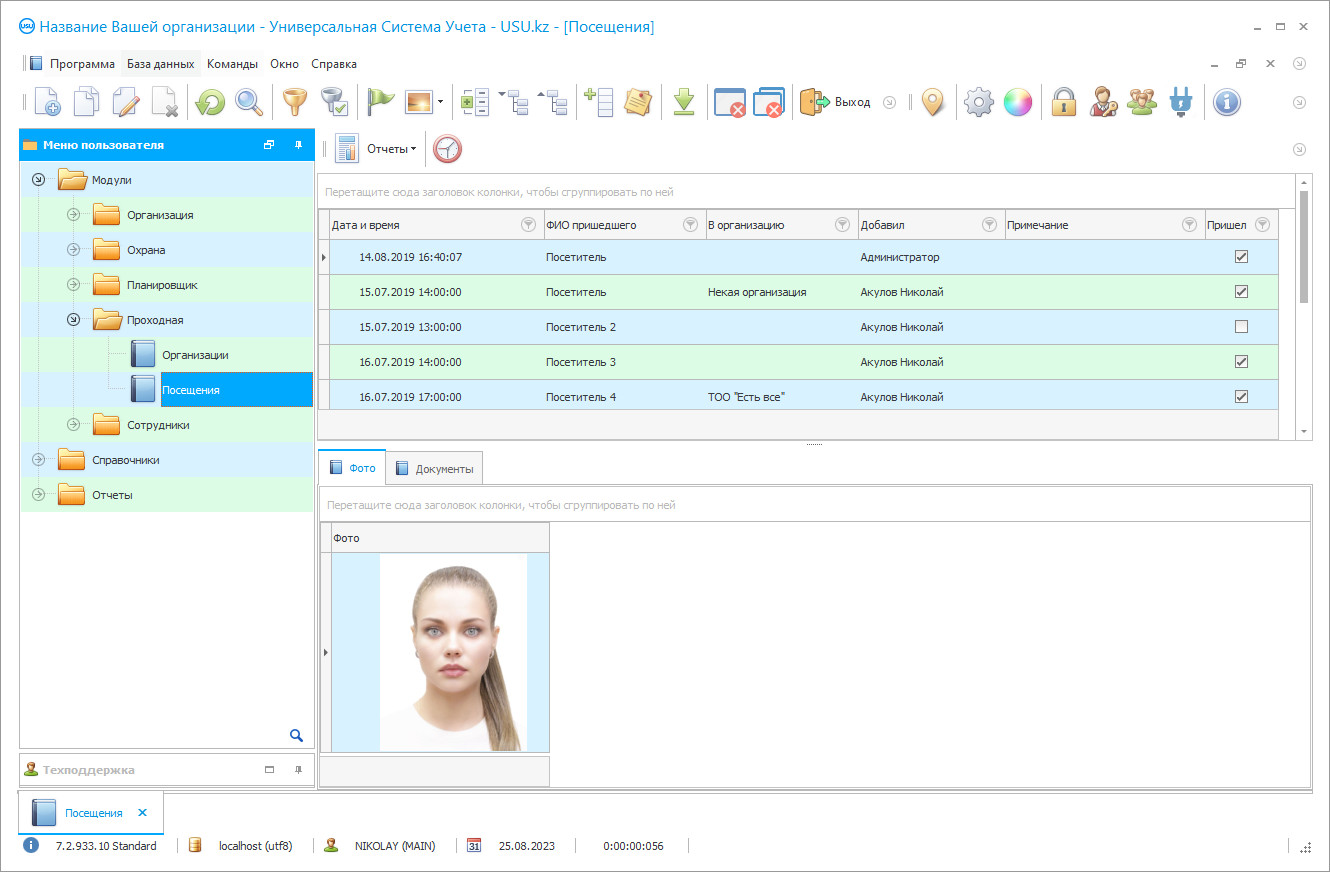
Visitor control is a mandatory aspect of the security work at the checkpoint of the institution. It is especially important to control the visitor at the checkpoint of business centers, where the flow of changing people is quite extensive. For the control of the visitor to take place efficiently and accurately, and most importantly, to fulfill its main task - to ensure security, it is necessary that the security service obligatory registration of each visitor in the accounting documents, be it a temporary visitor or a staff member. Visitor control is necessary not only for security purposes, it allows tracking the dynamics of visits of the temporary visitor or compliance with the schedule and the presence of delays among the company staff. To organize control of the visitor, as in principle, and any other control can be in two ways: manual and automated. If a few years ago, most companies kept control of visitor in special paper-based accounting journals, where records were made by personnel manually, now more and more enterprises are resorting to the help of automation services, which makes it possible to systematize processes at the checkpoint, making them more effective and efficient. The second option is preferable, and not only because it is more modern, but largely because it fully meets the assigned tasks of internal accounting, and also completely eliminates the problems that arise if control is organized manually. For example, the automatic registration of each visitor in a special automated program avoids errors in the records and also guarantees you the safety of data and the uninterrupted operation of such a system. In addition, by taking over most of the day-to-day functions, the software can free up security guards for more serious tasks. Automated control is easier and more comfortable for all participants in the process, saving both parties time. Hence, if you nevertheless decide to automate a security company, first we recommend that you pay attention to the choice of an automation application with which you will work. To do this, it is enough to study the market of modern technologies, where the direction of automation is currently actively developing, in connection with which software manufacturers offer an extensive selection of technological products.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-22
Video of visitor control
This video is in Russian. We have not yet managed to make videos in other languages.
In this essay, we want to draw your attention to the unique modern computer complex, which is ideal for internal control of the visitor by the company, and also has many other managing the security business capabilities. This visitor control program is called the USU Software system and it is available in more than 20 different functional configurations. This is done so that the application is universally applicable in various fields of activity. This scheme works, because the installation released by the specialists of the USU Software more than 8 years ago is still popular and in demand. It has won the trust of users and thus was awarded an electronic trust seal. A comfortable and easy-to-use program makes management of your company accessible even from a distance. It helps to establish internal control in all aspects: combine external and internal financial flows, solve the problem of visitor and staff accounting, facilitate the calculation of wages both at a fixed rate and on a piece-rate basis, optimizes the accounting control of company property and inventory processes, help streamline costs, establish the process of planning and delegating tasks, provide the development of CRM directions in the organization and much more. With the beginning of its use, the work of the manager is optimized, because now be able to control production processes while sitting in the office, despite the presence of accountable departments and branches. A centralized approach to control not only saves working time but also allows covering more information flows. Moreover, by automating the security agency, the manager able to control employees and the visitor, even if he had to leave the workplace for a long time. In this case, access to the data of the electronic database can be carried out from any mobile device that has access to the Internet. Very convenient for work in the field of security is the ability to create a mobile version of the USU Software that works in the official mobile application, which admits employees and management to always be aware of current events. The visitor control program actively uses its integration with various communication resources, such as SMS service, e-mail, and mobile chats, to promptly notify the necessary employees about a violation at the checkpoint or about a planned visit of a visitor. An unlimited number of people working in a common local network or the Internet can simultaneously use the universal control system. In this case, it advisable to create each of them their electronic account to delimit the workspace of the interface and set up personal access to menu sections.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
When organizing automated internal control of the visitor, barcoding technology and synchronization of the system with various equipment are increasingly used. For there to be a clear distinction between the temporary visitor and members of the collective of the protected enterprise in the process of accounting, it is necessary to first create a unified personnel base of the facility, where an electronic business card with full detailed information about this person provided to each employee. Coming to the workplace, each employee have to register in the program, which can be done by logging into a personal account, which is rarely used due to time costs, and you can also use a badge, which has a unique barcode generated by the application especially to identify this particular user. The identification code is read by a scanner on the turnstile, and the employee can go inside: very quickly and conveniently to each of the parties. To control unauthorized visitors, manual registration of data in the database is used, and the issuance of a temporary pass at the checkpoint, which contains basic information about the guest and his photo, taken there on a web camera, is presented. Such an approach to the internal control of a visitor allows recording the movement of each of them, based on which it possible, to sum up, the relevant statistics in the ‘Reports’ section.
Order a visitor control
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Visitor control
We recommend that you read about these and many other monitoring visitor tools on the USU Software website in the security configuration section. In case of additional questions, you can always contact our specialists for a free online Skype consultation.
The internal control of the visitor program can be used all over the world, thanks to the possibility of remote implementation and configuration of the application on your PC. The only starting to use the automated program condition is the presence of a personal computer connected to the Internet. The built-in glider allows not keeping in mind all the tasks necessary to complete the tasks, but transferring them into electronic format and efficiently distribute them among the personnel team. You can manage a security company remotely since the program's electronic database displays all the processes in progress in real-time. Considering the shift schedule of security personnel at the checkpoint, you can effectively monitor compliance with it and replace employees in the event of an emergency. The program interface may contain your company's logo displayed on the taskbar or on the main screen, which is carried out upon additional request by the USU Software programmers. The ability to create ‘hot’ keys makes the work in the program interface faster and allows quickly switching between tabs. Each employee's business card can contain a photo taken on a web camera for the convenience of tracking visits. Violations of the shift schedule and delays revealed during the internal control of a visitor are instantly displayed in the electronic system. The menu of a modern and laconic designed interface differs, among other things, by the fact that it consists of only three sections, with additional submodules. If employees work with the installation and adjustment of alarms and sensors, then they should work in a mobile application to display them in built-in interactive maps in case an alarm is triggered. Each person registered at the checkpoint of the enterprise on a special barcode scanner. By recording the visit of a temporary guest in the system installation, you can also indicate the purpose of his arrival and automatically notify the designated person about this via the interface. In the ‘Reports’ section, you can easily track the dynamics of attendance and form any management reporting against it. Based on viewing the dynamics of internal visits in the program, it is possible to identify on which days the most visitor come and put them on the entrance reinforcement.






