Operating system: Windows, Android, macOS
Group of programs: Business automation
Security management and control
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
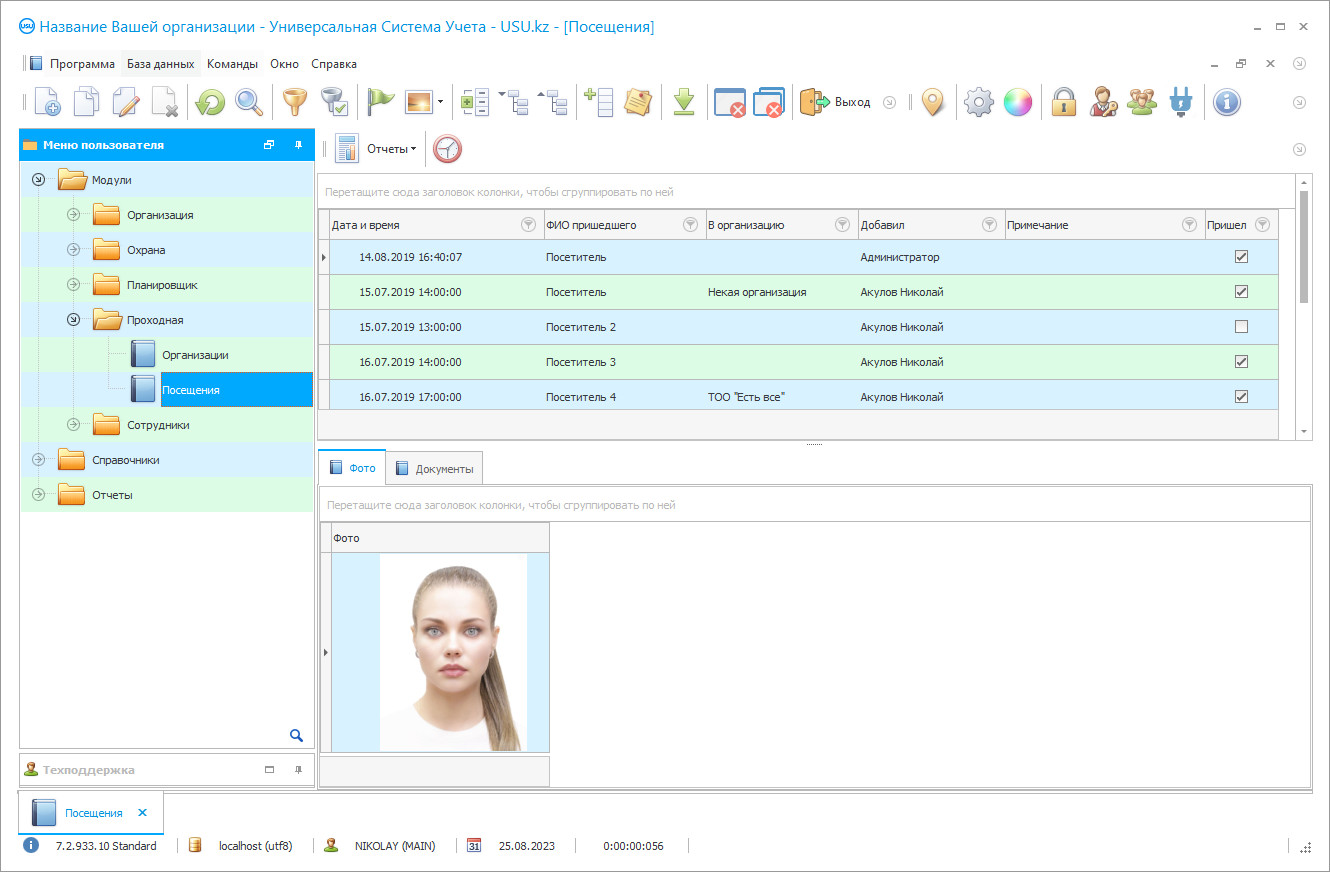
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
Management and control of security in the modern world are rather simplified with the help of various programs and tools. However, to find such a program that is right for you, meeting all your requirements and wishes, you need to go through the entire Internet and waste time. But, since you are reading this article, we are glad to notify you that you still managed to get a cool, easy-to-use, and easy-to-understand program. The team of developers of a universal management system presents to your review providing control, management, and monitoring security tool. The management and control of a security organization combine the activities of a manager, manager, accountant, auditor, and financier. In nature, this is a really time-consuming and energy-consuming point. To streamline and speed up the process of management and monitoring security, you just need to download our product.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-22
Video of security management and control
This video is in Russian. We have not yet managed to make videos in other languages.
What are the primary advantages of our management control system? First, the foundation is managed in one clack. By uploading an icon to your desktop, you get an optimized, state-of-the-art business control system. Without leaving doors, utilizing just your computer or laptop, you have the facility to remotely control and monitor your business. After all, work processes, payments, calls, or registration of new customers and orders are automatically saved in a single database of our smart tool. Secondly, in our intelligence mechanism, three main blocks unite the main sections and blocks in which you not get lost. These are ‘Modules’, ‘References’ and ‘Reports’. All the key work of management and control of the security organization takes place in the first block. Here you may enroll a new indent using the ‘Orders’ tab, add a new record in the management table and display the current information. To specify counterparties, the mechanism automatically directs you to the customer base. This is the ‘Clients’ tab. If the counterparty is in the database, you just need to select it, speeding up the process with a quick search. If the client is new, you can easily register him by specifying contact information, company name or name of the client, address, availability of discount conditions, and information about the contract. Next, you need to select the service provided from the catalog you have already filled out. In short, the ‘Modules’ block is endowed with such functions. Now let's move on to the description of the control processes in the ‘References’ block. To control the security using this block, you must complete this section once. Subsequently, calculations of quantitative, analytical, and financial indicators of protection are provided automatically. After all, it is with the help of reference books that the information security system itself carries out all the necessary calculations and analytics. In this block, you can divide all your services into categories, create special specific client's services prices, fix different currencies in the appropriate section, and much more. In the third block of ‘Reports’, statistics necessary for financial and management accounting are formed. The report of the register of payments shows an overall picture of the expenses and income of the security organization for the selected period. It should be marked that detailed tracking of the motion of funds furnishes an analysis of all fiscal materials, changes in spendings, and earnings for the previous times, respectively. In common, working with our development not only speed up all operations but also turns your daily routine into a pleasant pleasure.
Download demo version
When starting the program, you can select the language.
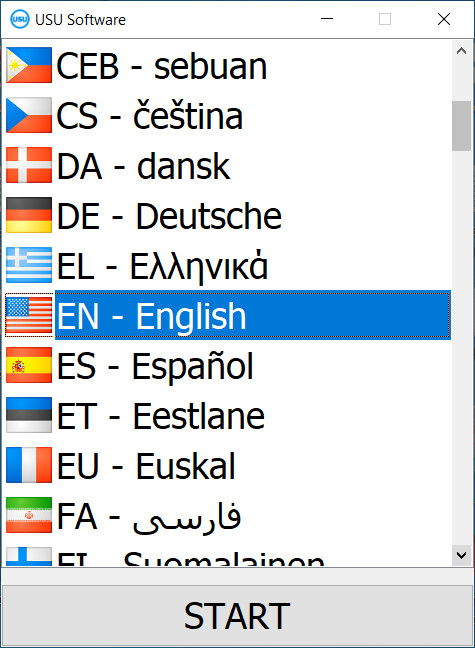
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
By keeping all the data about the guests of your security organization, our program forms a single client base. The management of a security organization greatly simplified and optimized, adding prestige and a good name to your company. With the help of counterparties quick search by the first letters of the name, phone number or other information, the workload of employees rather decrease. Dividing all prevailing customers into concrete categories following their bookings, characteristics, and history speed up the process of providing them with the trueness services, hereby improving management. The data bank of our tackle stores information about counterparties, phone numbers, addresses, and details. To streamline the control time of an organization, our tool automatically generates contracts and other documentation from templates. According to the shreds of evidence entered by the employee about various currencies in the security management information system, you can accept payment in any currency and convert it at your discretion.
Order a security management and control
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Security management and control
The function of keeping the history of all furnished services and bookings can serve as your storage for performing successive activities. Also, by continuing to furnish services to the same enterprise, you can gain devoted and loyal consumers. To expand your customer base and stay ahead of your competitors, you can factor in loyalty discounts. There are no obstacles and information mechanism boundaries, namely, you can register any number of services, consumers, and contractors. Management and control of a security organization involve reporting and analysis of revenue and spendings. Utilizing our monitoring mechanism, you can lightly generate records of any complexity. In the paymaster section, mechanical calculation of services is carried out and checks and invoices are issued. Compared to the personal factor, an automated management machine is capable of keeping track of debts, reminding of payments, and producing analytics. Understanding the distinction and differentiation of the organization's control services, our team can supplement and refine this system according to your wishes. Developed by the best programmers in their field, our unique security product can do much more!






