Operating system: Windows, Android, macOS
Group of programs: Business automation
Security company activities
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
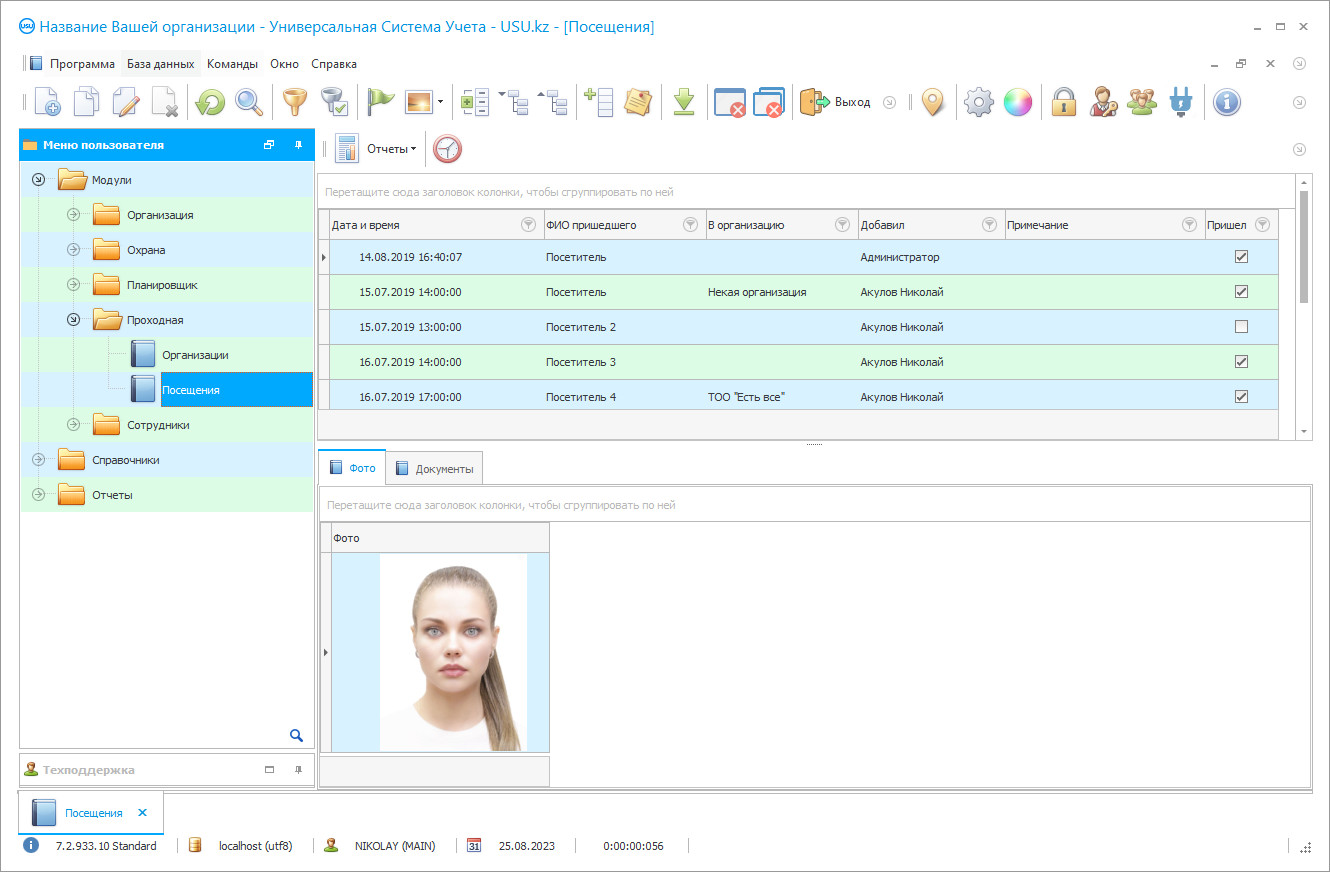
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
The activities of a security company and its success directly depend on how its internal accounting is organized. As in any other organization, manual or automated accounting can be applied to the management of the security company. However, realizing that security activities include a fairly wide range of services provided, it becomes clear that the first thing that the chosen management method should provide is fast and high-quality processing of information in any conditions. Automation of the security company, which can be carried out by introducing a special automated application, help to ensure it and free staff from maintaining special logs manually. Unlike manual accounting, using the automation of activities, you cease to depend on the human factor, since most of the routine functions can be taken over by software and additional devices with which it integrates. Computerized activities of a security company program are able to qualitatively improve its management, giving the manager a centralized continuous control over all aspects. Also, by automating security activities, you receive a systematization of work processes, allowing you to make the work operational and efficient. This consistency allows avoiding the appearance of errors during the entry of records and serving as a guarantor of the reliability of the data. The advantage of an automated approach to the management of a security service provider is that all accounting activities are transferred to electronic format, which means that the data continuously accessible and their security guaranteed. Contrary to popular belief, the automation procedure is not complicated and expensive. Modern vendors are actively developing this area, offering a wide range of different options, competing both in price and in the offered functionality. Thus, you can make a choice of software that suits you in all respects.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-22
Video of security company activities
This video is in Russian. We have not yet managed to make videos in other languages.
An excellent ready-made automating of the activities of a security company technological solution is the USU Software system, which is the development of the USU Software company. Having been implemented more than 8 years ago, it immediately won the trust and love of new users, thanks to which the USU Software team was awarded an electronic sign of trust. The unique characteristics of the program open up new opportunities in business management, making it easier and more comfortable. In addition, the universal security system can be used at any company, no matter what activity it leads, because manufacturers have developed more than 20 different modules, whose functionality is selected for different areas of business. The versatility of the application is not the only thing that sets it apart from its competitors. The great advantage of this platform is its simplicity and accessibility, expressed in the style of interface and menu design. You can deal with the internal structure of computer software on your own, having devoted a couple of free hours to training. Pop-up tips built into the interface as an electronic guide able to optimize the initial acquaintance with the product installation, and the USU Software specialists have created detailed training videos to each configuration, which you can view completely free of charge on our website. Continuous communication between the employees of the security company during the activity is the key to more accurate accounting and efficiency of actions. The system is able to provide it through the use of multi-user mode and synchronization with various communication methods. The multi-user mode assumes that all employees of the company able to use its capabilities at the same time, provided that there is a connection between them via a local network or the Internet. It is also preferable to this that each user has his account, which allows quickly registering in the program, tracking activity, and also regulating the setting of personal access to different categories of information. At the same time, users able to freely exchange messages or files sent directly from the interface, thanks to the integration of the platform with various services (SMS, e-mail, mobile messengers, PBX station).
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
It is very convenient to control the activities of a security company using our automated program since it takes into account all the specifics of this area. Firstly, it is convenient to create and maintain a single client base in it, where a special account is created for each counterparty. All known data on cooperation with this company are manually entered in the record: its details, contact person, availability of a contract and its terms, services provided, expected dates of services, cost of their provision, and information on debts or past payments. Such a record is a kind of business card of the counterparty. The same electronic notes are created in the case of a security agency working at the entrance for all visitors, while the company staff is registered in the database using a special badge, and temporary visitors receive a one-time pass, generated and printed according to the template saved in the ‘Directories’. The integration of software with a webcam is useful in creating an instant photo to fill in a temporary pass. Secondly, the electronic database of the application does not limit users in the amount of information, thus, being at the post, employees can record every event that has occurred in it. If the activity of a security company consists of equipping objects with alarms and various sensors, then with a certain set of the universal system, you able to observe online all indicators transmitted automatically from these devices. In the same case, it easy for the management of the security service to keep records of such equipment and carry out timely inspection and repair. In the built-in planner of the platform, you can plan the activities of personnel, delegating certain tasks and powers to them, putting down the dates of the project in the calendar, and automatically notifying the performers through the interface. All these and many other tools you can use to develop your business, thanks to the automation of security activities through the USU Software.
Order a security company activities
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Security company activities
The USU Software is an indispensable its head or owner assistant. In addition to all the listed qualities, USU Software offers rather favorable cooperation conditions and very pleasant product prices. The security service conducts its activities within the framework of an automated program easily and comfortably, controlling every process that takes place. In the ‘Reports’ section, you can easily view the statistics of hours worked by your employees at a particular facility. The automated program makes it much easier for the security company to control its employees since their activities can be tracked by personal accounts. The system supports the automatic generation of various types of receipts and required security activities' forms. The functionality of the ‘Reports’ module provides you with visual financial statistics in a short time. With the help of automation, it is easy to achieve optimization of the manager's work, thanks to the centralization of control and the ability to conduct it remotely, from any mobile device. An audit of all actions performed by the personnel help to track whether they have had over time and how many hours were worked with a specific counterparty. In the application, you can record even one-time installation of alarm services or the protection of any event. Thanks to the integration of the program with any modern devices, you can keep a record of triggered alarms. Built-in interactive maps allow you to tag both your customers and employees working from the mobile application on them. Carrying out security activities at the checkpoint of the company, you can print passes for full-time employees. A making payments convenient program in the USU Software allows making cooperation with your company comfortable. All employees work from a single database, but in different accounts, which makes it possible to delimit the workspace of the program interface. You can carry out the activities of a company on an automated platform in different languages of the world, but the main one, by default, is Russian. The automated application store the history of cooperation to each counterparty to whom you have provided security services in the past.






