Operating system: Windows, Android, macOS
Group of programs: Business automation
Security management
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
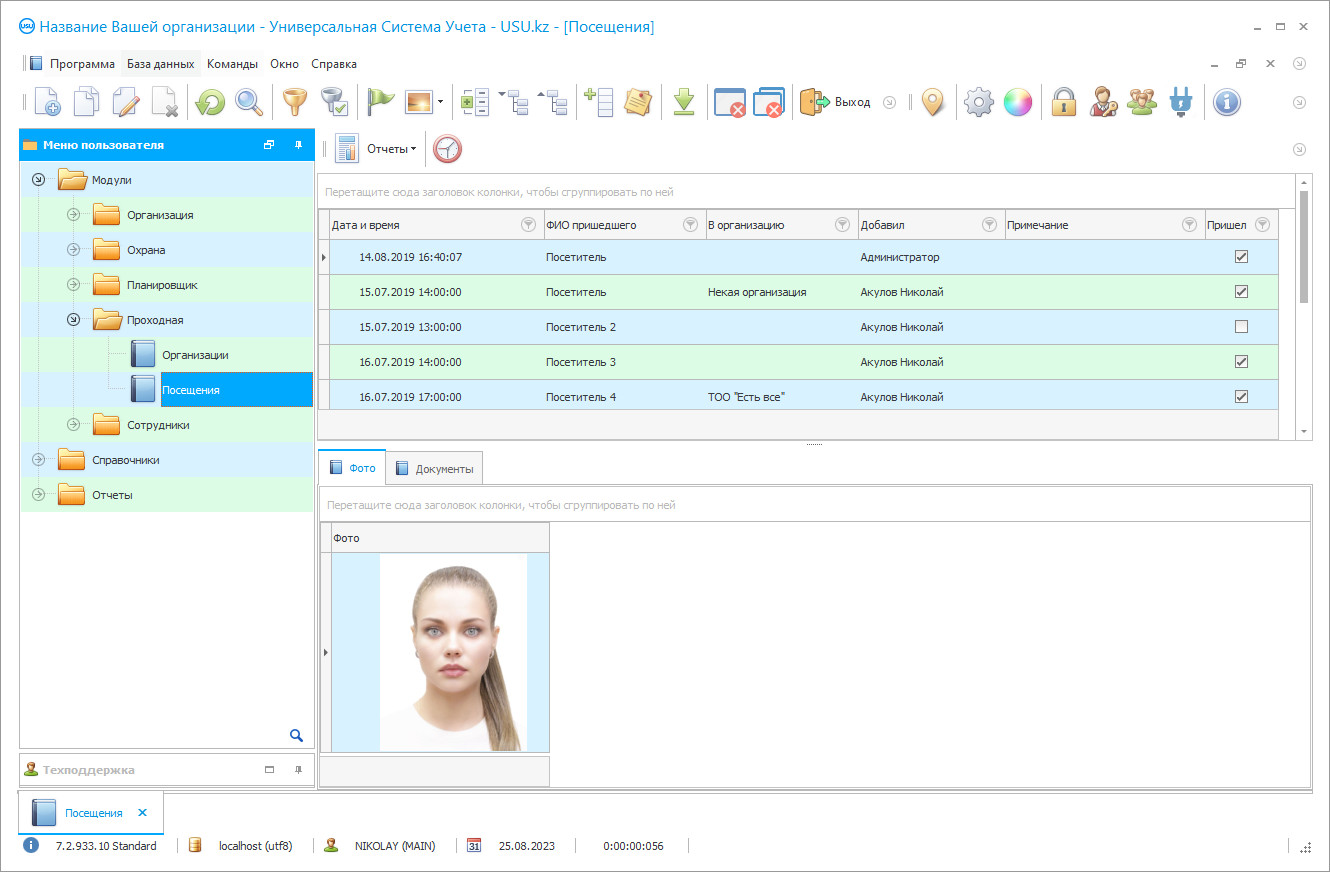
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
Security management is a process that requires increased attention from the heads of all protected enterprises and companies. This process is also of great importance for the security organizations themselves. The former mainly control the quality of services and the effectiveness of the work of the guards. Management of a security company is more complex in its structure since it consists not only of external control of services but also of painstaking internal control over the activities of personnel. Security, no matter how numerous or small in number, needs high-quality and professional management, since its effectiveness depends on this, and as a result, the safety of people and the protected object. The rules and instructions are established by the head of a security company or organization, if it is about their security, then the order of the security activities is established by the director of the organization. There is a lot of legal information that can be applied in practice when creating a security organization and a company, but the issues of managing it are practical issues, and here the search for methods and tools is everyone's personal business. If you try to do everything in the old and time-tested ways, you can get certain results, but you cannot count on the high efficiency and quality of security services. In the management of security, clear and competent planning is of no small importance. Each security officer must clearly understand his duties and tasks, know what the consequences can be for neglecting them. At every stage of the work of the company, control is important. It is necessary to improve the quality of services, raising the qualifications and training of personnel, teaching security in modern technologies, and methods of ensuring security. Internal control over the work is no less important - duty accounting, service checks, assessment of the correctness of the implementation of actions and instructions. These are the main components of full-fledged management of a security company or an enterprise security service.
How to put these statements into practice? You can use the old method of paper reporting. At the same time, the security officers devote most of their time to compiling reports and reports on a variety of topics - from registering visitors to reporting on the use of special equipment, gasoline consumption, and undergoing briefings. It can be difficult to understand such reports, to find the necessary information, especially if some time has passed since the moment of their compilation. Management can also be made difficult by the human factor - the real state of affairs does not always get on paper, some of the important company information may be lost. There is another very delicate and painful issue in the management of security - the issue of corruption. Human weaknesses open up great criminals opportunities, and there are a large number of methods to force a security specialist to compromise principles and violate instructions - these are threats, blackmail, bribery. None of the old methods can solve this problem.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-22
Video of security management
This video is in Russian. We have not yet managed to make videos in other languages.
Management will be more correct, high-quality, and efficient only if it solves the designated tasks quickly and easily. In other words, it should include planning, continuous monitoring, assessment of the quality of services, security firms, personnel records and reduce the influence of the human factor. All this is at the same time. There is only one way out - to fully automate all the main processes.
This is the solution offered by the USU Software system. Its specialists have developed providing security and security companies management activities. The program effectively solves the issue of time - it automates document flow and reporting, freeing staff from the need to conduct paper correspondence with their superiors and record every action on paper. The freed time can be used to carry out basic professional duties. In turn, this comprehensively contributes to improving the quality of the firm's security services.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
The USU Software deal with expert planning, help to draw up a budget, duty schedules and also provide control over all work processes. The manager receives a powerful modern and easy management tool based on a clear understanding of the real state of affairs in the company, on statistics, analytical data, and strict reporting. The management program from USU Software creates functional and detailed databases, automatically draw up the necessary documents, including contracts and payment documentation, financial statements, to each direction of the firm's work, each security service, and each security officer, it possible to receive detailed information that helps to manage correctly, accurately and profitably. The system automates the access control and the work of the checkpoint, simplifying the tasks of security and excluding any corrupt actions because it is impossible to ‘negotiate’ with the program, it cannot be intimidated and deceived. In the basic version, work is possible in Russian. The international version provides the ability to manage security in any language of the world. It is possible to order from the developers a personalized version of the platform, which works taking into account all the specifics of the company. The management program automatically generates and constantly updates the databases. The databases are not limited to one contact information, they contain the entire history of the company's interaction with the person, orders, projects, agreements, and requests. You can add files of any format to the management system without restrictions. This provides the security with detailed instructions with photos, videos, models and drawings of objects, photographs of visitors, which help the system identify anyone who is trying to enter the territory of the protected object.
The management program can process any amount of data without loss of performance, dividing them into convenient modules, categories, and groups. For each group, a quick search is possible - by visitors, personnel, date and time of visit, purpose, transport, and cargo, order, object, or client. Control management access automated. The system reads the data of electronic passes, bar codes, quickly analyzes and identifies information, allows or denies access to the object. When uploading information about the search with photographs, the system quickly ‘recognizes’ people from this group, if they appear at the protected facility.
Order a security management
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Security management
The program facilitates personnel management to a minimum. Automated entry sends data to the service sheet, and based on this information it clear who and what time came to work, took over the shift, left the workplace. The head of the security service or shift able to see in real-time where the employees of the company are, what they are doing. At the end of the reporting period, the management system provides information on the personal performance of each. The management program maintains detailed financial records, recording income and expenses, including spending on security needs.
USU Software protects trade secrets and intellectual property. Access to the control system is possible only within the scope of authority and competence by personal login. The security officer does not receive financial information, and the financier not able to see the information about the protected object. The storage period of information is not limited. The backup is carried out without stopping the software, in the background. The program creates a single space in which all departments, company offices, warehouses, and security points are united. The staff increases the speed of interaction, and the manager receives monitoring and management tool in real-time. The system has a convenient built-in scheduler. The manager receives all reports, statistics, and analytical data with the frequency that he assigns. The security management development can be integrated with video surveillance cameras, telephony, company website. The security program keeps inventory records at the expert level. The security software can organize mass or individual mailing by SMS or e-mail.






