Operating system: Windows, Android, macOS
Group of programs: Business automation
System for control of security
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
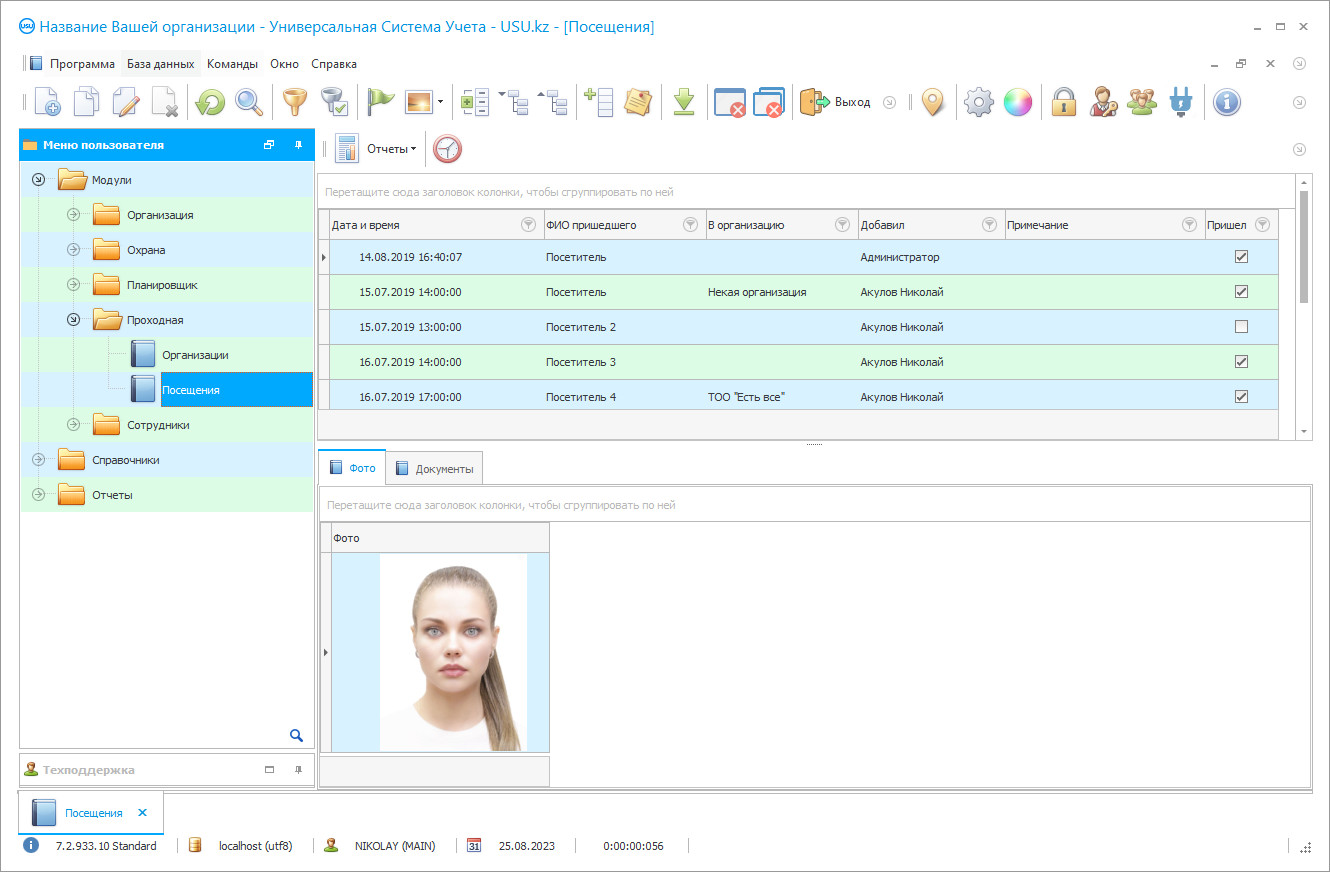
A universal security control system (hereinafter referred to as USU Software) is designed to optimize security on the territory of the institution. Maintaining a security monitoring system requires attention to detail and discipline. The organization of a security system does not make sense if it is not possible to maintain strict control over the implementation of all instructions by employees. USU Software specialists have developed a system that helps organize the maintenance of the security control system. The multi-window interface of the system has a pleasant and thoughtful design, where all data is divided between modules. Each module in the system carries certain functions. The system is aimed at the standard personal computer user, because we strive to create quick mastering of the system's capabilities comfortable environment. This helps the rapid implementation of the control system in the enterprise. The USU Software system is recommended by the best specialists in the field of IT technologies since we offer a professional application that successfully implements the automation of work processes in many areas of activity. The system provides the security of the building control, thus, it provides the use of video surveillance, scanning documents at the entrance to the building, and instant notifications. The security guards conduct their activities according to a predetermined duty schedule. The duty schedule is created in the USU Software system using a single employee database, which is formed in a separate module. A unified security control system is convenient in that it conjoins several points and branches of the enterprise at once. This thoughtful approach to combining control points in one database significantly optimizes the process of collecting and analyzing information. A separate pitch ‘Reports’ presents a variety of kinds of marketing and financial dissects. Here, using filters, you may set the reporting period, choose the necessary report filters. The finished paper can be printed, expressed, sent by e-mail. Moment messaging to e-mail directions, phone applications are other handy functions that facilitate fast communication betwixt departments of the enterprise or for the quick transfer of information to its customers. For nowadays users, the variety of interface themes design a pleasant surprise. Everyone is able to find a design for their taste and mood. The particularity of the interface of the USU Software system is that it is very plain in terms of acquiring and further use. It is designed specifically for the modern user of a personal computer because USU Software crew strive to improve the behavior and control of their clients' activities by optimizing the main work processes, while not overloading the complexity of the system. Users can familiarize themselves with the system. It is very detailed by reviewing a demo version. The service is guaranteed free of charge. The system can be left on the website. The modern security program of the enterprise is a tandem consisting of the professionalism of the personnel and the presence of a modern control application. It is the proper application that is the framework for the competent structuring of the incoming and outgoing information flow. The USU Software control development transforms the usual security service into an automated and circumspective algorithm of actions, where each employee is in his place and knows how to draw up a particular situation in working order. If you have doubts and would like to receive advice, our managers respond to all your questions.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-22
Video of system for control of security
This video is in Russian. We have not yet managed to make videos in other languages.
Security management development has a lot of following pleasant features: machinery and equipment accounting, circumspective communication between all departments, control of financial expenses, income and other expenses accounting, preparation of the necessary reports by the guards on the implementation of all instructions, the use of any peripheral office devices, a large selection of marketing analysis of the quality of security work reports, administrative control of clients' debts, instant mailing to email addresses, configurable data backup function, a large selection of interface design themes.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
The entire list of services is kept in one database. For each buyer, you can selectively mark the provided list of services. A single database of maintaining the work of employees, building a work schedule. Automation of booking order forms, contracts, contractors, where all the necessary data collected, and other documents. Parsing of the popularity of the concern in comparison with other rivals. Each paper created in the system can have its own image. Notification of the necessity to update flow contracts for a new reporting season. Smartphone employees and customer control applications are available to order. You can try connecting communication with payment terminals service. Adoption of payment in any cash, in currency, and by money transfer. Multi-window space for better intuitive system evolution. The structure of the system is oriented towards the ordinary user of a personal computer. The act in the system is provided in most languages of the world. A multi-user system admits several managers to work in it at once. The act in the system is provided by the user who has an extra login and access password. The search system provides quick access to the information of interest. In addition, regarding the installation of a security control system, you can contact all contact numbers and e-mail addresses indicated on the site.
Order a system for control of security
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!






