Operating system: Windows, Android, macOS
Group of programs: Business automation
Program for security workers
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
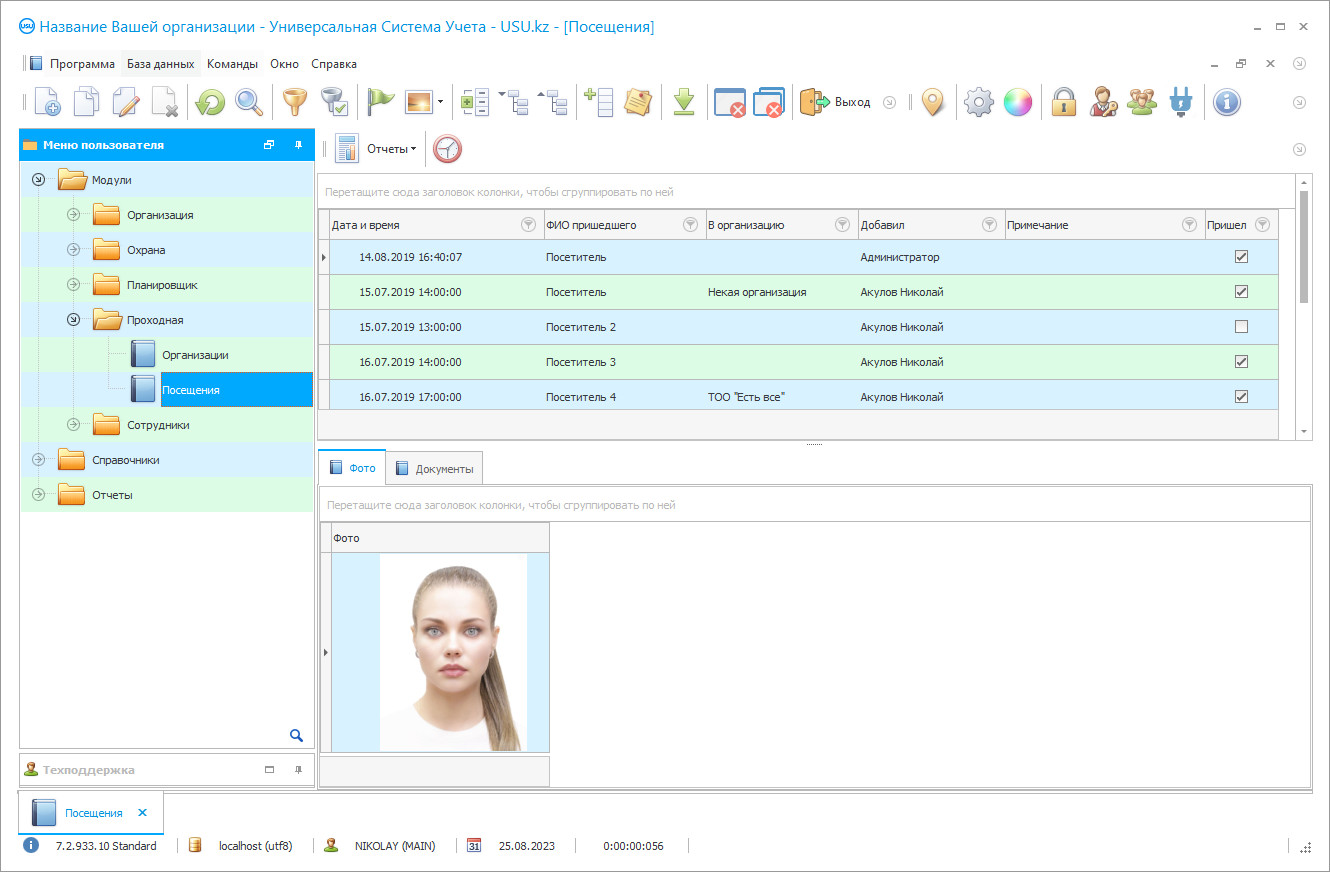
The security workers program is a modern solution in the organization of security activities. The well-being and economic safety of the company directly depend on the quality of the security work and thus increased attention should be paid to security. Previously, security activities were organized and managed by ineffective paper reporting methods. The security guards, who spend most of their working hours writing reports and keeping logs of visitors, shifts, transfer of special equipment, examinations, and keys, did not have time for personal professional growth and fulfillment of their direct duties. Modern security requirements are different. It is important for workers of security services and security structures to be attentive and polite, competent, to know the structure and location of the alarm, panic button, to be able to protect people, and, if necessary, to carry out detention, evacuation, and first aid. Is it possible to improve the quality of services if a multivolume paper routine is burdened with a heavy burden?
A smart solution is to install a security workers program. But any program not suitable for the full-fledged activity. We need a system that takes into account all the nuances of the official activities of workers of the security structure. The ideal program should have powerful planning, accounting, and automation capabilities. It should save people from paperwork, free up as much time as possible for workers to fully carry out their duties. At the same time, the program should help to solve another delicate problem - the problem of the human factor. It is impossible to ‘negotiate’ with the program, blackmail it and intimidate it, it does not get sick and does not suffer from human weaknesses, and thus the use of automation reduces the likelihood of corruption among security personnel and their violation of instructions and rules. For the proper organization of the work of security, it is important to download such a program that provides the manager with the ability to plan and detailed control, as well as all analytical data on indicators of the quality of security services, so that this information can be used for management.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-23
Video of program for security workers
This video is in Russian. We have not yet managed to make videos in other languages.
The possibilities of using 1C and other automation systems are multifaceted, but, unfortunately, they do not cover all the nuances of the service activities of security workers. They solve only part of the urgent tasks related to reporting, but they do not eliminate the possible corruption factor and do not provide in-depth analytical information.
A surprisingly simple and functional solution was offered by the USU Software program. It has developed a program that optimally takes into account all the needs and problems of security workers. It can be downloaded from the developer's website free. The demo version, available for two weeks' use, helps you evaluate and test the powerful potential of the software to make an informed decision about purchasing the full version of the program. It is not difficult to install the program, it is enough just to inform the developers of your desire by e-mail.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
The program from USU Software fully automates the workflow. The head of the security service or company receives full analytical and statistical information about the services, financial reports of any complexity, as well as detailed reports on the activities of each security officer. The program maintains a report of shifts and shifts by itself, in parallel entering data into service timesheets. This helps you see how much a particular employee actually worked, make a decision on bonuses or calculate his salary. The program can be downloaded in any version. You no longer need to download the full version, it is installed by the developer's representatives remotely, connecting to the customer's computer via the Internet. If an organization has its unique specifics of activities, developers create a personalized version of the program that is best suited for a particular organization. The security workers program is easy to download, install. It has a quick start, a clear and simple interface, anyone cope with it, even if his level of technical training is not high. The program is useful for any companies that have their security services, security departments, security firms, and enterprises, as well as law enforcement agencies and law enforcement agencies. The security worker's development is able to work with the information of any volume and complexity without losing performance. It divides data into convenient categories, modules. To each, you can get comprehensive statistical, analytical, and reporting data. The program forms and constantly updates databases - clients, employees, visitors. All necessary additional information can be attached to each point of the base - photographs scanned copies of identity cards. The program quickly identifies any person based on photographs.
The program from USU Software help to fully automate the work of the throughput and throughput mode. This solves the influence of the human factor in corruption issues. The program reads barcodes from the badges and automatically registers incoming and outgoing. This ensures that workers are kept in mind work hours and work discipline. The manager is able to get a full report on the activities of security workers and other specialists. The program shows the personal effectiveness and usefulness of each. This can be used to create a program of rewards and punishments, for making personnel decisions, calculating wages and bonuses. The program provides data on what types of security services are provided most often. You can download and print this information to help you plan the employment of your security personnel. The program works quickly, in real-time, even if large amounts of data are loaded into it. Using the search box, you can instantly search for people, employees, workers, visits, date, time, the purpose of visit, marking of exported goods, and state registration numbers of vehicles. The limitation period does not matter. The program from USU Software automatically generates all documentation and reports. The manager configures the frequency of receiving reports or see the data in the current time mode. Each report in the form of a table, graph, all indicators diagrams can be downloaded and saved for further work.
Order a program for security workers
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Program for security workers
The software unites employees of different posts, departments, branches, offices, divisions of the company within one information space. The employees themselves get the opportunity to interact more quickly, and the manager sees the real state of affairs to each post and employee. The complex provides high-quality warehouse accounting, displaying the balance and consumption of GMR, special equipment, radio stations, materials, raw materials. If something runs out, the system warns you about it in advance. Any inventory information can be downloaded at the right time. The program helps the accountant and auditors to see all the financial information by providing detailed reports on the flow of funds on accounts, expenses, and income.
The system from USU Software supports the ability to download, save and transfer files of any format. Photos, videos, and audio recordings can be downloaded and used in official activities to improve the quality of services. The entrance to the program is differentiated. Each employee receives it under his authority and level of competence. The accountant not able to download the visitor data at the checkpoint, and the security guard does not see the financial statements. Backups occur at a specified frequency in the background. You do not need to stop the program to save new information. The program integrates with the website, telephony, payment terminals, and video surveillance cameras. Workers can additionally download and install a specially designed mobile application, and the leader useful to the updated version of the ‘Bible of the modern leader’.






