Operating system: Windows, Android, macOS
Group of programs: Business automation
Control of a checkpoint
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
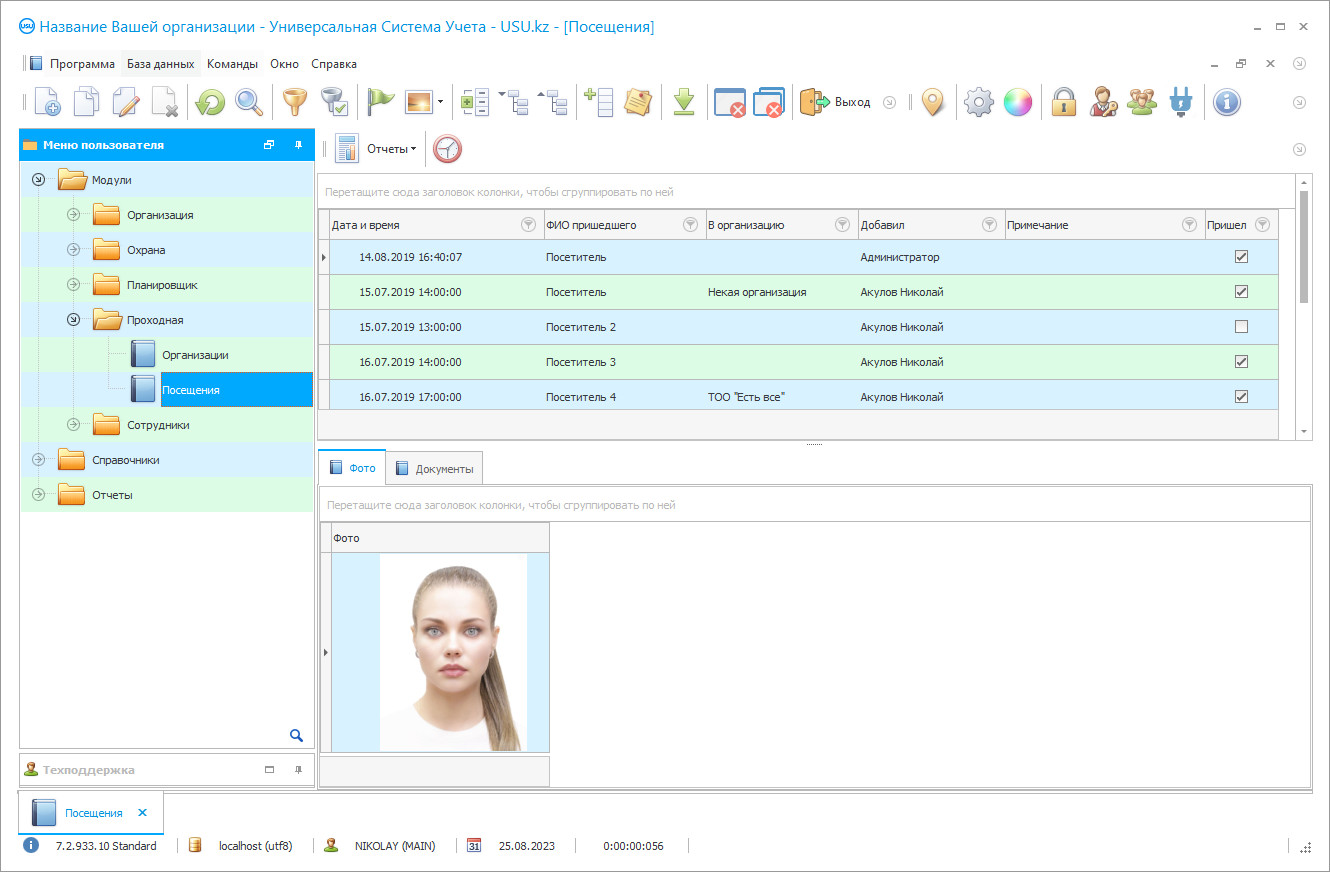
Control of a checkpoint is an important process on which the security of an enterprise, company, organization heavily depends. The checkpoint is the entrance gate and is the first to meet employees, visitors, customers. By the organization of work at the checkpoint, one can judge the company as a whole. If the guard is openly rude and is not able to answer the questions of visitors and advise them, if a rather large queue of people eager to get inside is lined up at the entrance, and the guard is in no hurry, then hardly anyone can have confidence in the organization to which the visit was made.
Special attention should be paid to the control of the work of the checkpoint. It shapes the image of the company and contributes to its security — both physical and economic. Modern entrepreneurs, realizing the importance of the issue, are trying to equip their checkpoints with electronic reading devices, detector frames, modern turnstiles, and CCTV cameras. But no technical innovations and achievements should be effective if they work at the checkpoint is organized very badly, there is no control and accounting, the professionalism of the security officer raises serious doubts.
The conclusion here is simple and clear to everyone — no matter how technically equipped a company's or enterprise's checkpoint is, without competent control its activities won’t be effective, and security will not be guaranteed. There are several approaches to control. It is possible, in the best Soviet traditions, to issue a bunch of accounting logs to the guard. In one, they’ll enter the names and passport data of visitors, in the other — the next shifts, in the third — information about incoming and outgoing transport, exported and imported cargo. A couple more notebooks need to be allocated for instructions, accounting for the receipt of radios and special equipment, and also provide a journal that stores information about employees — active, dismissed, in order to know exactly who to let into the territory and who to politely refuse.
Many people practice this method in combination with the achievements of modern technologies — they ask the security not only to write all the above but also to make a duplicate of the data into the computer. Neither the first method nor the second protects the company from loss of information, does not increase security, and does not contribute to the effective control of the checkpoint. The only sensible solution is full automation. This solution was proposed by a company called USU Software. The digital tool for checkpoints, developed by its specialists, can, at a professional level, organize automatic electronic control over all processes occurring at the entrance to the company. The control system automatically registers incoming and outgoing employees, visitors. Our program instantly processes data from turnstiles that read bar codes from employee passes. If there are no such passes or badges, then the system from our developers makes them by assigning bar codes to the personnel of the organization according to their degree of admission.
In practice, it works like this. The program scans the code, compares it with the available data in the databases, identifies the person at the entrance, and immediately enters into the statistics information that this person has crossed the border of the checkpoint. If there is a CCTV camera on the entrance program, it’ll record the faces of all incoming and outgoing people, indicate the exact time of entry and exit. This will help, if you need to establish a history of visits, find a specific visitor, find a suspect, if an offense or crime has been committed at the enterprise. The office of the checkpoint can also serve the needs of the personnel department and accounting. The system from our developers automatically fills in several digital logbooks — keep counting visitors and record information in the worksheets of each employee. This provides detailed information about the time of coming to work, leaving it, actually working period, which is important for making personnel, disciplinary decisions.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-22
Video of control of a checkpoint
This video is in Russian. We have not yet managed to make videos in other languages.
What are the functions of a security officer with such a smart checkpoint, you ask? In fact, they are minimal. The program frees a person from the need to conduct multi-volume reporting on paper but leaves them with the opportunity to make certain notes and notes in the system. The security guard can reveal all his professional skills and talents. If there is no need to focus on the visitor's face, remembering who it is and where it is going, on checking and rewriting passport data, then it's time to practice observation and deduction. The security guard at the checkpoint can leave comments and observations to each visitor, this can be useful in a variety of situations.
The software manages not only the checkpoint but also the activities of all personnel, since it will not be possible to negotiate in the most amicable way with an impartial system if the employee is late, tried to bring in or take out something forbidden, lead outsiders, attempts will be immediately recorded, reflected in statistics and suppressed.
This control system is based on the Windows operating system. The trial version can be downloaded for free from the developer's website. Usually, the allotted two weeks are enough to appreciate the powerful functionality of the software. The full version is installed remotely via the Internet. The basic version works in Russian. An advanced international version helps to organize control in pretty much any language. Optionally, you can order a personal version of the program, which works by taking into account certain nuances and specifics of the activities of the checkpoint in a particular organization.
USU Software has several important advantages. First of all, it does not make mistakes, does not hesitate, and does not get sick, and therefore clear control at the checkpoint is always ensured, at any time of the day. It makes decisions very quickly because it is able to work with any amount of data. Even if they are large, all operations are completed in a matter of seconds. Another advantage is simplicity. The software from our development team has a quick start, an intuitive user interface, and a nice design, everyone can work in this control system, even those who do not have a high level of knowledge of information technologies.
The software can be useful to all organizations that have a checkpoint. It’ll be especially useful for those firms and enterprises that have large areas and have several checkpoints. For them, the system easily unites all of them into one information space, facilitating the communication of guards with each other, increasing the speed and efficiency of activities.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
The program automatically generates the necessary reporting data on the number of visitors per hour, day, week, month, it’ll show whether employees violated the regime and discipline, how often they did it. It’ll automatically form the database as well. Regular visitors are no longer needed to order special passes. Those who have crossed the turnstile at least once should be remembered by the program, photographed, and by all means recognized the next time they visit. The system makes it easy to manage accounting at any level. It automatically generates and replenishes databases. Can divide them by guests, employees, by the time of visit, by the purpose of the visit. You can attach the information in any format to each character in the database — photographs, videos, scanned copies of identity documents. For each, a complete history of visits for any period can be saved.
The data in the control system is stored as long as required by the internal regime of the organization. At any time, it’ll be possible to find the history of any visit — by date, time, employee, by the purpose of the visit, by the notes made by the security guard. To save data, the backup is configured at an arbitrary frequency. Even if it is carried out every hour, it won’t interfere with activities — the process of saving new information does not require even a short temporary stop of the software, everything happens in the background. If two employees save the data at the same time, then there is no conflict in the program, both information is recorded correctly.
The program provides differentiated access to preserve information and trade secrets. Employees get access to it by personal login within the framework of their official powers. For example, a security guard at a checkpoint won’t be able to see the reporting information on the control of the security service, and the head of the security service should see the full picture for each of the existing entrances and for each employee in particular.
The head of the company can carry out competent control, having the opportunity to receive the necessary reports at any time or within the established target dates. The program automatically generates them and provides them by the desired date in the form of a list, table, diagram, or graph. For analysis, the previous data for any period can also be provided. Automatic reporting of the work of the checkpoint itself eliminates the annoying mistakes of guards when drawing up reports, reports, and reminders. All data will correspond to the real state of affairs.
The head of the security service is able to see in real-time the employment of each security guard at each checkpoint. Within the framework of control, they’ll be able to track his actions, his observance of instructions, requirements, working hours. Everyone's personal performance should be reflected in the reports and can be a compelling reason for dismissal, promotion, bonuses, or wages if the employee works on a piece-rate basis.
Order a control of a checkpoint
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Control of a checkpoint
The control software won’t allow you to take out from the territory of the enterprise what should not be taken out. It maintains
careful inventory control, it contains data on the labeling of goods, products, raw materials, and payment. The cargo to be removed can be immediately marked within the system. If you try to take out or take out otherwise, the program prohibits this action. The system can be integrated with telephony and the organization's website. The first gives an amazing opportunity for every guest who has ever left contact information to be immediately recognized. This control program shows exactly who is calling, the staff should be able to address the interlocutor immediately by name and patronymic. It is pleasant and enhances the prestige of the company. Integration with the site opens up the possibility of online registration, receiving up-to-date information on prices, opening hours. Also, when ordering passes, a person can get them in their personal account on the site.
The program can be integrated with video cameras. This makes it possible to receive text information in the video stream. So the security service specialists should be able to get more information while controlling the checkpoint, cash desks. The control program can at a professional level keep records of everything — from the income and expenses of the organization to the volume of sales, own expenses, advertising efficiency. The manager should be able to receive reports on any module and category.
This program has the ability to promptly communicate with employees through a dialog box. Control will become more efficient, and the quality of staff work is higher since it is possible to install a specially developed mobile application on employees' gadgets. An advanced control system can communicate with payment terminals, any trading equipment, and therefore the security guard will see the data on payment for the exported cargo when the cargo leaves the territory of the enterprise, and the employees of the finished product warehouse automatically mark the write-off. This program can organize mass or individual sending of SMS or emails.






