Operating system: Windows, Android, macOS
Group of programs: Business automation
Checkpoint automation
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
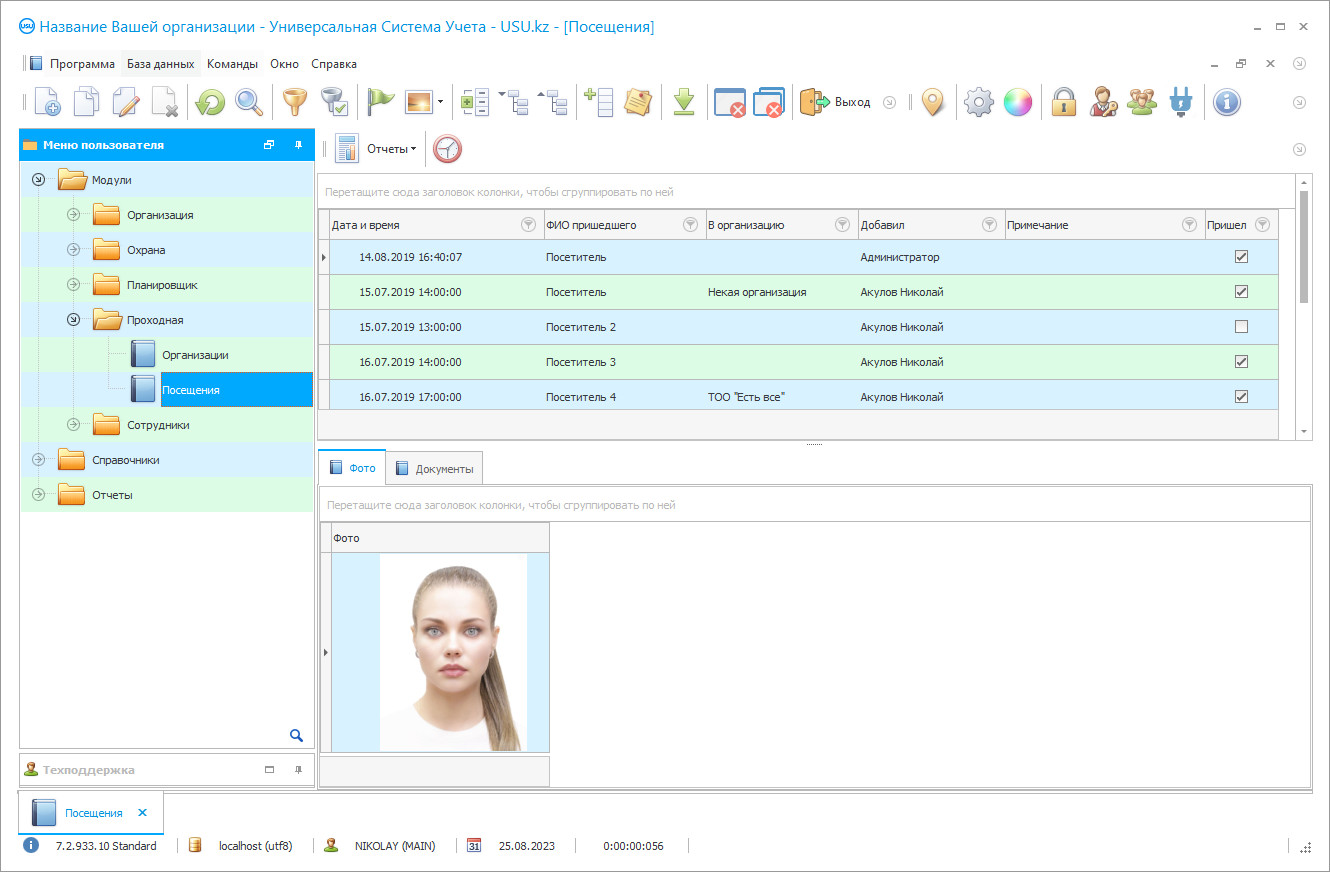
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
Automation of the company’s checkpoint is necessary for any institutions that have checkpoints that track the movements of employees of a given institution, as well as visitors who receive temporary access to the territory of the facility. Programs designed for automation of the checkpoint are not yet so widespread, as many firms still prefer to maintain a special accounting log manually, assuming that automation services are quite expensive. In fact, manual tracking of the checkpoint is extremely ineffective, due to the excessive influence of the human error factor on such process. After all, the logging is carried out by personnel, whose work and its effectiveness directly depend on the workload and external circumstances. Due to inattention and lack of consistency, employees might make mistakes in the records, and they might simply be missed by not paying attention. That is why, for conducting a checkpoint, an automated approach is urgently needed, which must be able to minimize the influence of the human factor, replacing it with artificial intelligence of computer software and special hardware equipment. Due to the extensive development of the production of the automation system, which it has received recently, manufacturers offer a huge selection of programs, including for automation of the entrance, which makes such service available to every owner. An automated checkpoint allows you to effectively keep track of all visitors, storing data for each visit for a long time. With it, you’ll be able to track the dynamics of staff attendance, statistics of visitors' visits, employee compliance with the work schedule, etc. The main tools used in the work of an automated checkpoint are bar coding technology and devices associated with the program, such as a bar code scanner, a printer, and a web camera. The opportunities offered by the automation of the checkpoint make it possible to adjust the accounting of many aspects of a protected company or a business center, making it easier and more comfortable to control its activities.
We are pleased to offer you a ready-made solution for the automation of a checkpoint in the form of USU Software, which was developed by our development team, taking into account the latest techniques in such an area. The unique characteristics of this program allow you to carry out many functions and establish internal accounting for the attendance of the enterprise by both employees and strangers. And now a little about the application itself, it is absolutely universal for any enterprise, since it has more than twenty types of thought-out functional configurations developed for each business segment. A wide range of available automatic functions allows you to control not only the checkpoint, but also aspects such as financial flows, inventory control system, personnel, payroll, and the like. Every employee should be able to work in it, despite his initial qualifications, knowledge, and department. The simple design of the interface allows you to master it in a matter of hours, without prior training, which is facilitated by the presence of tooltips. Also, if necessary, you might use the free training videos that are posted on our official website. The ability to personalize the user interface via settings makes it comfortable to use. Separately, it is worth mentioning such program options as multi-user mode, thanks to which an unlimited number of users can work in its modules, performing different work. A prerequisite for this approach is the presence of an Internet connection or a common local network, and it is also desirable to apply the delimitation of the workspace by creating personal accounts for each employee. By creating a personal account, you’ll not only be able to view the actions performed by a person, but also regulate their access to various categories of information in the menu. Thus, you can protect the confidential information of the company from prying eyes. The gatehouse automation program is easily interfaced with various modern devices that can optimize the workplace of each employee. These can be web cameras, a scanner, a turnstile, and security cameras. This makes the work of the control personnel more efficient and faster, and also gives the control accuracy. It is also important to use such resources as SMS, e-mail, automatic telephone exchange, mobile messengers in internal communication between program users. Using these tools, the security should be able to inform the management about violations or the arrival of a visitor to them.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-22
Video of checkpoint automation
This video is in Russian. We have not yet managed to make videos in other languages.
The possibilities of automated control of the checkpoint are quite large because the program is able to register each visitor by creating a special electronic record. Staff members whose employment is registered in the ‘Directories’ folder of the software installation can be checked using a special badge with a unique bar code. This serves as a kind of registration in the USU Software on arrival, in the records of which the employee's business card and arrival time are displayed. To register unauthorized visitors in the automation program, a temporary pass is used. To form it, the guard manually enters data about the visitor and can attach an additional file to this entry, in the form of a scanned identity document, or a photo, whipped up through a web camera. Thus, in the program it’ll be possible to create a separate folder for freelance visitors, tracking the purpose of their arrival and dynamics. These are just a few tools that can be used to automate a gateway in a company or even a business center. Using an automated approach to its management, you can easily ensure the security of your facility.
Software from this development team with a configuration for the protection of objects is suitable for any company related to security activities: private security companies, security services, private security guards, checkpoints, and so on. For a more detailed acquaintance with the application, we recommend that you familiarize yourself with its characteristics on the official website of our company.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
Automation of a private security company can be carried out remotely, for which you must provide our programmers with access to your personal computer, which has an Internet connection. Automation of the checkpoint makes it easy to track the observance of the working hours by staff and put them down automatically in an electronic time sheet.
Our specialists offer you a high-quality product, each parameter of which has been thought out taking into account the specifics of managing different areas of activity. In the built-in scheduler, you can keep track of shift schedules for representatives of the security department of your company. USU Software’s configuration for gate automation is suitable both for one company and for a business center, where dozens of different companies are located. Automation of a security agency includes accounting for security alarms and automatic reading of their sensors, thanks to the synchronization of devices.
Order a checkpoint automation
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Checkpoint automation
You can use this automation program in any language convenient for your staff. Thanks to automation, the digital database of the program can keep records of each employee who regularly has access to the territory of the enterprise, where basic information about his personality and position is stored. This program for automation is capable of forming contracts for the protection of objects with various companies. The use of this universal system makes it possible to apply flexible tariff scales for calculating the cost of services with different companies. Since the security agency most often works on a system of monthly payments from clients, you can easily track the presence of debts and over-payments in the ‘Reports’ section. Piecework calculation of wages for security guards can be carried out automatically by the software based on the hours worked. Automatic control and tracking of the checkpoint readings of various sensors, the triggers of which are reflected and stored in the electronic database of the application. The head of the security bureau should be able to plan further actions for each object in the built-in planner. The ability to register each employee in the checkpoint management software using a badge allows you to track all their delays and possible overtime, which helps to issue a recalculation of wages.






