Operating system: Windows, Android, macOS
Group of programs: Business automation
Organization of security control
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
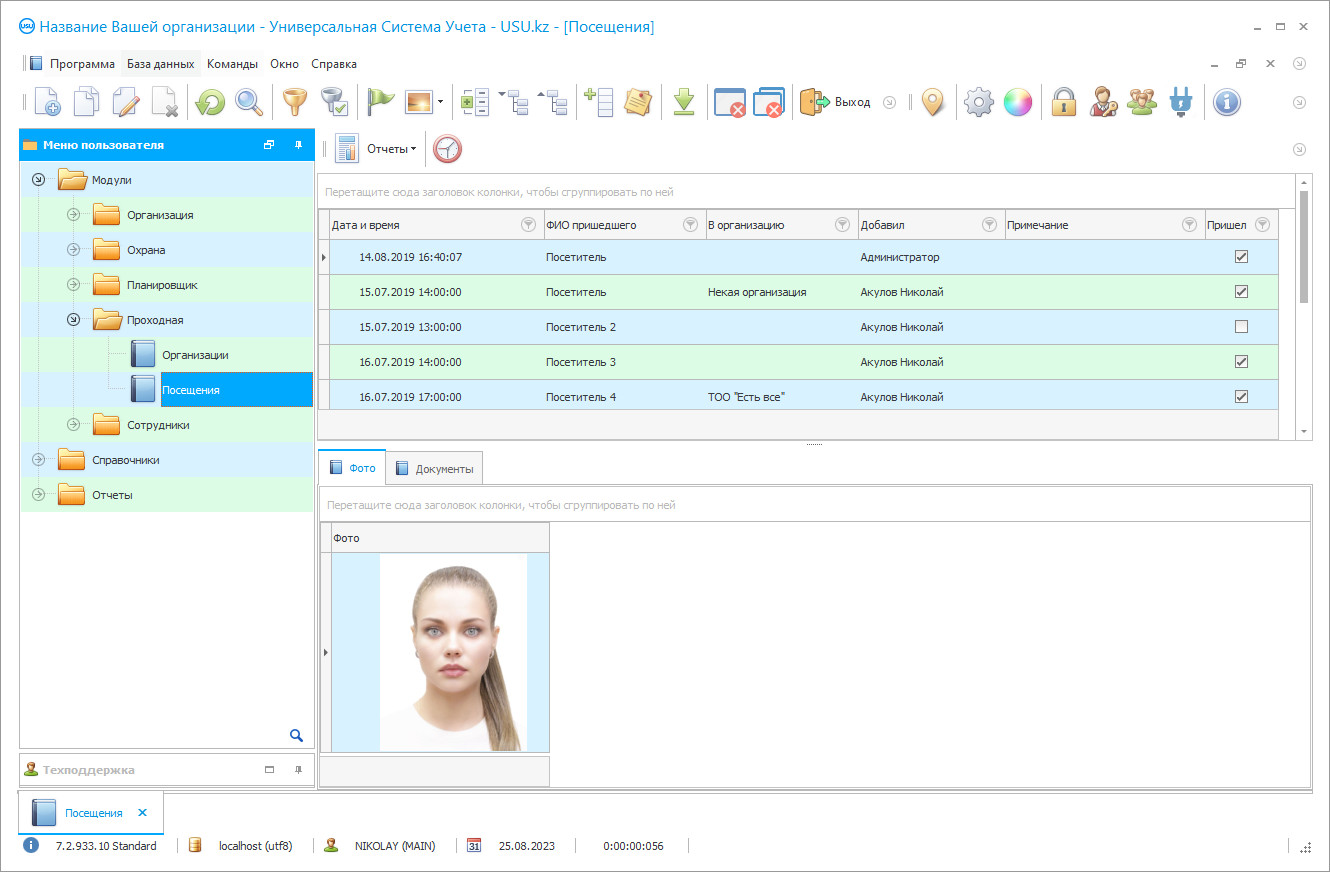
Organization of security control is the most important issue both for the heads of security companies and for the heads of enterprises and organizations that use security services. The effectiveness of the work of the guards depends on how correctly this control is organized. And effective security is a guarantee of the safety of property, trade secrets, intellectual property, as well as a guarantee of the safety of guests and staff.
Modern concepts of protection differ from the concepts that were adopted several decades ago. And although the essence of the work has remained the same, the mechanisms, tools, requirements have changed. Previously, a security guard with a newspaper or a book in his hands, bored and not knowing what to do with himself, was a harsh reality. Today, such a security guard is unlikely to suit anyone. The specialist of the security organization or the employee of the security department must be polite and physically competent. He is the first to meet customers, and therefore must be able to quickly navigate and suggest where it is best to contact the visitor with his question, direct, help.
The security function is responsible for monitoring the incoming and outgoing of the organization, the personnel, as well as the incoming and outgoing vehicles. The security specialist must know how the alarm works and works when it is necessary to resort to the emergency call button of the police. In addition, the security officer himself must have enough knowledge and skills to, if necessary, carry out the detention himself, evacuate people from the facility, and even provide first aid to the injured.
It is these security services that are considered to be of high quality, they are in demand. And to achieve this goal, one cannot do without organizing security control. Managers who begin to tread the path of optimizing security work face two challenges. It can be difficult to set up correct reporting in the first place. If you do everything in the most old-fashioned way, requiring the guard to maintain dozens of forms and accounting journals, fill out a colossal amount of documentation, then most of the working time is spent on paperwork. At the same time, the guards cannot fully fulfill their basic duties. And finding the information you need in a pile of papers can be extremely difficult, and sometimes even impossible.
If you require the guards to additionally enter reports into the computer, then even more time will be spent than with written records. At the same time, the efficiency does not increase, and the very question of preserving information in proper form is a big question. In both cases, everything converges to a key link — a person, and they tend to make mistakes, forget, and miss important details.
The organization of security control is also difficult to deal with because there is almost no way to eliminate the human factor in issues that require an impartial solution. Therefore, it can never be guaranteed that an attacker will not be able to come to an agreement with the guards, or, in extreme cases, intimidate them and force them to violate the instructions.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-21
Video of organization of security control
This video is in Russian. We have not yet managed to make videos in other languages.
The organization of control of a security organization or its own security service will be successful only if the human factor in it is excluded and minimized. This can be achieved by automating all processes. Control of a security organization can be made simple, fast, and accurate if automation methods are applied correctly.
Such a solution is offered by the USU Software development team. Its specialists have developed unique software that contributes to the comprehensive control of security, as well as other areas of activity. The system offered by our team automates document flow and reporting. All analytical and statistical data is generated automatically, which relieves security guards against the need to maintain a huge number of written forms of the report and gives them the opportunity to devote more time to their main professional activities.
USU Software keeps records of shifts, shifts, counts the hours actually worked, and calculates wages if employees work on piece-rate terms. The control organization system automatically generates databases, calculates the cost of security services, draws up contracts and payment documents, and displays information on each area of the security organization's work. The reports generated by the software will show which types of security services are more in demand by customers — escorting goods and valuables, bodyguard services, guarding facilities, patrolling, working with visitors at checkpoints, or others. This software keeps records of all economic performance indicators, including the security's own expenses for organizing work. All this will help to build a competent and effective control system. The program from our developers in the basic configuration works in the Russian language. If there is a need to configure the system in another language, you can use the international version of the software. The trial version can be downloaded for free on the developer's website. A two-week period, which is allotted for its use, will be quite sufficient for the security of the enterprise, the security service, or the security agency to assess all the capabilities of the software and its potential. Installing the full version does not require significant time expenditures, waiting for a representative to appear from the developer company. Everything happens remotely, the developers establish a remote connection with the customer's computers, present the capabilities and install the control system.
If a security company, security service, or the company itself has a special specificity in its activities, developers can create a personalized version of the software that will be optimal for organizing control, taking into account all the specific features.
You can use the program to organize security control at an enterprise of any field of activity, to ensure control of the activities of law enforcement agencies, law enforcement agencies, as well as private security organizations. The control program can work with any amount of data. It divides them into convenient categories, modules, groups. For each of them, at any time, you can get all the statistical and reporting data — by visitors, employees, customers, by vehicle registration, by date, time, the purpose of visits to the organization.
The control system databases are formed and updated automatically. They include more than just contact information. Each person, whether it is a visitor or an employee of an organization, can be attached with information about an identity card, photographs, bar code data of a pass. The program quickly recognizes and identifies a person, making a note of his visit with a reference to the time.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
The program will create customer databases for security agencies. An entire history of interaction will be attached to each one — requests, completed projects, requests. This system shows which of the clients prefers certain types of security services to a greater extent. This helps to make profitable and interesting commercial offers for both parties.
The program automates the access control and the work of the checkpoint. It provides the organization of control of visitors both at the visual level and at the level of qualified automatic face control, reads the data of electronic passes, bar codes. Such a program cannot be negotiated, cannot be intimidated or forced to violate instructions. The control organization system can be loaded with data in any files and formats. For example, it is possible to upload photos of the protected object, three-dimensional schemes of the perimeter, emergency exits, video files to the customer data. The security service can add photographs of employees, as well as guidelines for the search for criminals and offenders. If one of them tries to enter the territory of the protected object, the program identifies them by the image and lets them know about it.
The control program will keep a detailed financial report — on income, expenses, displaying all expenses for the security structure's own needs. This data can become the basis for competent optimization and will serve as a great help for the manager, accountant, and auditors.
Data in the control system is stored for as long as required. The backup function is configured automatically. The process of saving information does not require stopping the program, everything takes place in the background.
No matter how large and voluminous the data in the program, it works quickly. The search for the required document, instructions, agreement, information about the passage through the checkpoint, visit, or removal of the cargo can be found in a matter of seconds for any category of request — by date, time, person, place, name of the cargo. How long it was, does not matter — the control program remembers everything.
The system unites different departments, divisions, branches, security posts, offices, warehouses of the organization within a single information space. Employees of various departments will be able to quickly interact, exchange data, and the manager will have full control over everything that happens in the organization.
Order an organization of security control
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Organization of security control
The monitoring program shows the personal performance of each employee, including security guards. It will record the time of coming to work, leaving, the number of hours worked and shifts, the number of work performed. This information will be updated automatically. At the end of the reporting period, the manager will receive detailed reports, according to which he can make a decision on dismissal, promotion, bonuses.
A convenient built-in planner helps the manager to draw up a budget and monitor its implementation. The HR department of the organization will be able to plan activity schedules, automatically filling out
time sheets and service forms will take place. Any employee from a security guard to a manager will be able to plan their working hours more efficiently. If something is forgotten, the control system will notify about it. The management of the organization, the head of the security department can configure the frequency of receiving reports, which is convenient for them. The reports themselves are available in the form of lists, graphs, tables, diagrams. This control program can be integrated with video cameras, which will provide text content in the video stream. This function is convenient for additional control over checkpoints, cash desks, warehouses.
Access to the system from USU Software is differentiated, excluding data leaks and misuse of information. Each employee receives a login, which opens up the opportunity for him to receive information from certain modules that are admissible according to the level of competence. The accounting department will never receive the rights to manage the checkpoint, and the security will not have access to financial and management reports.
The software keeps expert records in warehouses and in the production of the organization. At any time, it will be possible to obtain data on the availability and quantity, and the guards will be able to see in real-time the goods paid for, subject to removal from the territory. This will make shipping easier. The system can be integrated with the website and telephony of the organization, which opens up wide and unique opportunities for building relationships with customers and partners. Also, the software can be integrated with any warehouse and trade equipment, and payment terminals.






