Operating system: Windows, Android, macOS
Group of programs: Business automation
System for security enterprise
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
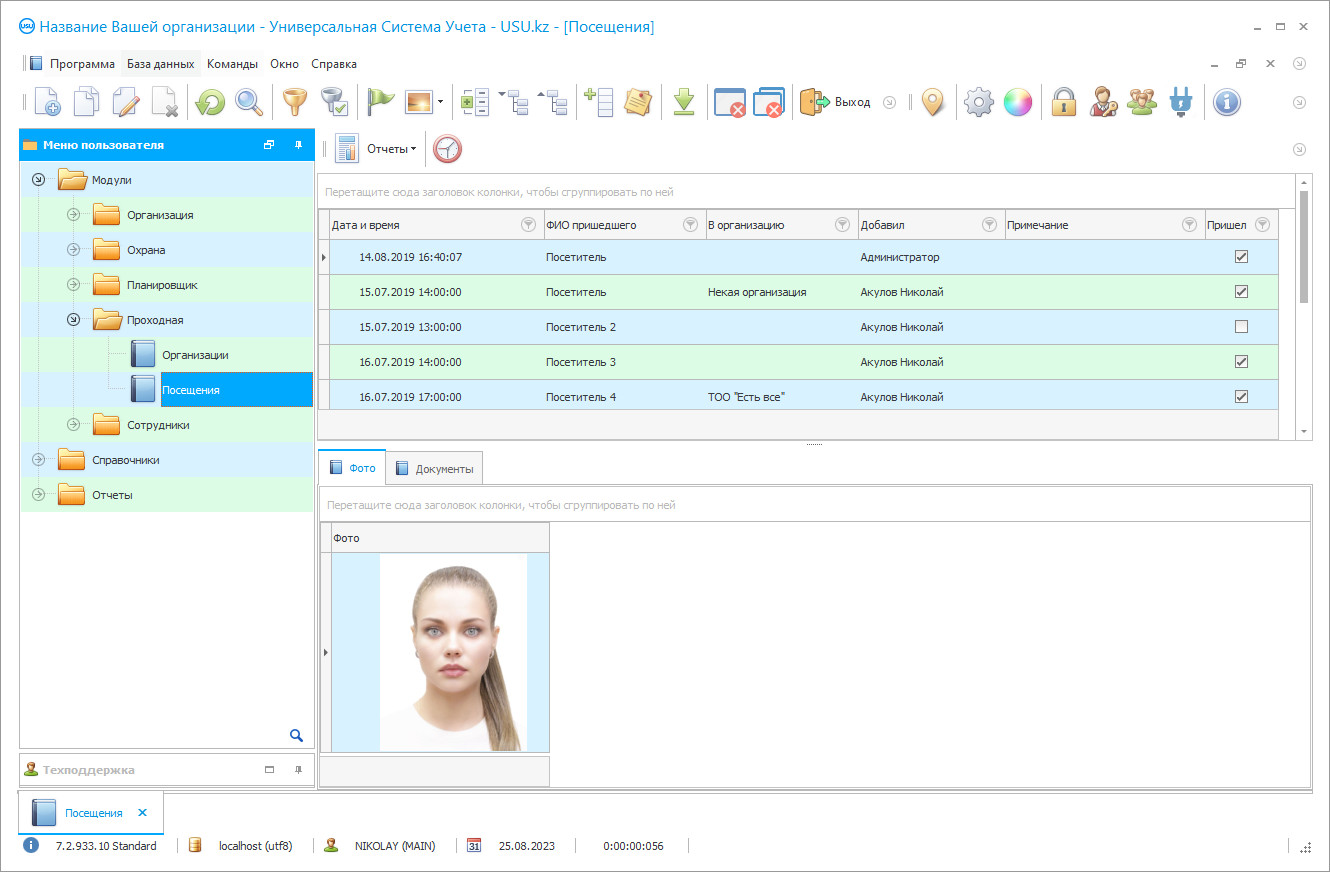
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
An automated security enterprise system and its application is an excellent way to optimize work activities to efficiently perform work tasks. The work system of a security enterprise must have all the necessary options to regulate and improve work processes to effectively and timely perform tasks to ensure safety and security. The functionality that the system of organizing a security enterprise and conducting activities should have should fully correspond to factors such as the needs and preferences of the enterprise, as well as take into account the specifics of the enterprise work. The organization of work at a security concern has certain features and specific nuances characteristic of this type of activity, thus, the use of an automated system is important. The system can be an excellent assistant in regulating and improving work processes, in which the enterprise performance grows, like other indicators. The benefits of using various information programs have been proven by any enterprise, so do not underestimate the popularity of information technology. Modernization has firmly established itself as a leader in the activities that enterprises aspire to. Hence, the use of automation organizing work in enterprise programs the right decision. The job of a security organization is to ensure security in companies, it requires adherence to certain rules and the application of various measures, thus, such work processes as accounting and control can be entrusted to the system product. As a result, the functioning of the enterprise not only improves but also brings excellent results in the form of an increase in many performance indicators.
The USU Software system is a modern automating work processes system aimed at optimizing the actions of any enterprise. The USU Software can be applied in any field of activity, including security companies. Moreover, the system has special properties and unique functions. A feature of the system is the possibility of correcting functional settings, which allows paying attention to the needs and desires of the client, as well as the specifics of procedures in security organizations. The implementation and installation of the system are fulfilled in a short time, do not require additional costs, and do not affect the operations of the organization.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-22
Video of system for security enterprise
This video is in Russian. We have not yet managed to make videos in other languages.
With the assistance of the USU Software, you may carry out operations of different kinds, such as financial and managerial activities, management of a security enterprise, quality control of security services, the enterprise of the security personnel work, implementation of document circulation, mailing of different kinds, carrying out warehouse management processes, planning, budgeting and forecast, implementation of financial and economic analysis and audit control, control over the organization of labor activities (scheduling work, shifts, etc.) and much more.
USU Software system - efficiency and reliability in the development and success of your organization!
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
The system can be used in any organization, including security ones.
USU Software is multifunctional but at the same time a simple and convenient system, the use of which does not cause problems and difficulties. The system has many distinctive special functions, including monitoring security equipment. Enterprise management is organized using different kinds of control, paying attention to the characteristics of the type of activity. Automation of workflow makes it probable to regulate and reduce the utilization of labor resources and time, facilitating the procedure of maintaining, processing, and processing documents. Implementation of database creation. The database can include an unlimited amount of information, which can not only be stored and processed, but also can be transmitted quickly. Thanks to the use of an automated system, your enterprise able to easily improve the quality of the provided security services, which affects the formation of a positive image of the enterprise. Control over security facilities, security guards, management of equipment necessary to ensure the implementation of security and safety tasks. In the system, you can register passes of employees and visitors, keep records on them and control receipt and change.
Order a system for security enterprise
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
System for security enterprise
USU Software allows collecting and maintaining statistics, as well as implementing statistical and analytical evaluation. In the system, you may control the work of each worker of the organization separately. All work procedures fulfilled in the USU Software are recorded, providing an opportunity to control the work of personnel and identify shortcomings in the work. Implementation of economic analysis and audit control, the results of which can help in making more effective management decisions. The application of the system contributes to a more efficient enterprise of labor with the growth of all labor indicators. The system allows organizing and conducting mailing in various ways: by e-mail and via SMS messages. The management of the access control is notable for certain complexity. The fact is that realization of the checkpoint mechanism regime is based on the application of ‘prohibitions’ and ‘restrictions’ with subjects crossing the boundaries of protected objects to assure the interests of the company. Such a mechanism must be flawless in terms of compliance with the requirements of the current legislation. The USU Software crew of specialists provides a wide range of services and quality services.






