Operating system: Windows, Android, macOS
Group of programs: Business automation
Control over security at the enterprise
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
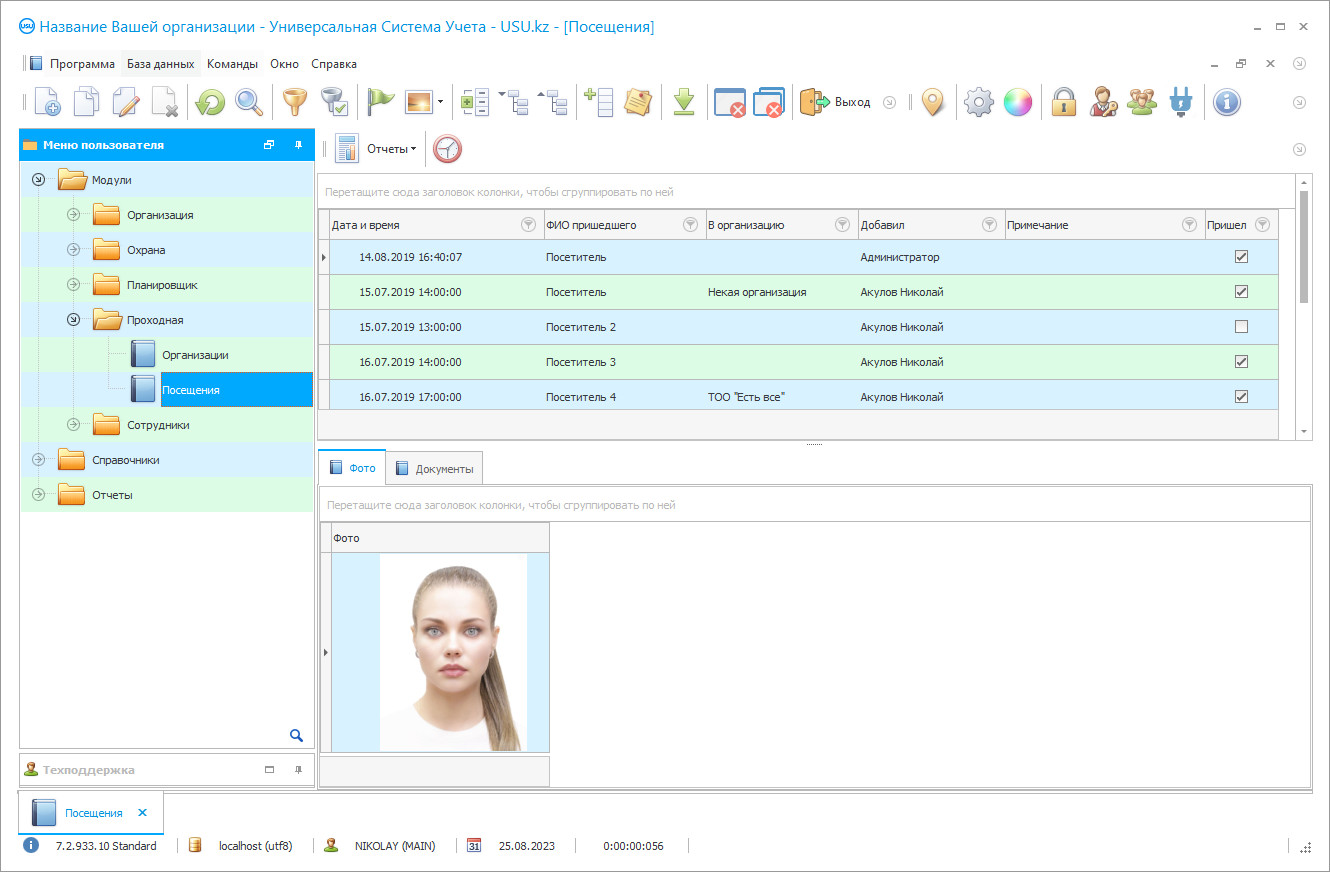
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
Control over security at any enterprise is a rather difficult task. Usually, it falls on the shoulders of the head of the enterprise or chief of the security service. It all depends on whether the company has its own security department, or whether the company uses the services of a private security agency. But no matter how the form of organization is decided, the need for control is always there. The security of the enterprise has special responsibilities. It provides control of checkpoints, records visits, attendance of employees, prevents unauthorized access to protected areas. Security controls the dispatch of goods by the enterprise, keeps records of the entry and exit of vehicles. Particular attention is paid to the control of their own work — compliance with the schedules of rounds, inspection, taking under the protection of premises, duty schedules, transfer of shifts.
Control over security in the enterprise can be continuous and constant. The safety and well-being of the organization and each of its employees, economic security depend on this. Therefore, the functions of the guards cannot be underestimated. Control can be organized in different ways. The simplest, but most irrational, is paper reporting. The security workers have to record all stages of their activities in journals and accounting forms, write a huge amount of papers. In fact, a security guard needs to devote a full work shift to writing reports in order to take everything into account. With this kind of management, there is no need to talk about full control. An employee may forget to enter information, confuse something, lose the logbook or it may even suddenly be stained with tea. If there is a need to conduct an urgent internal investigation, it can be difficult to find a grain of truth in the abundance of logs.
The second method is more modern but even less rational. With it, the guard also keeps written records but additionally duplicates the data into the computer. This partially solves the problem of the tea-stained logbook, but does not solve the problem of spending time on reporting — it takes even more time if anything. Both methods are not ideal, since they are revolved around the human error factor.
It is important for the enterprise to solve one more problem when monitoring security. There is a possibility that an attacker should find mechanisms of pressure or persuasion to force the guard to compromise principles and close eyes to certain actions. So often valuables are taken out from the enterprise, prohibited items and substances are brought into the territory, and the passage of strangers is a normal thing. Late employees, for a fee, persuade the guard to indicate a different time of their arrival at work. Even if a controller is placed next to each guard, which in itself is irrational and unreasonable, the likelihood of such violations still remains. Are there options for a comprehensive solution to all the problems of quality control over security at the enterprise? Yes, and this is the automation of security activities, in which the human error factor is minimized to practically zero. The security application at the enterprise was developed by the specialists of the USU Software. USU Software provides high-quality and impartial control over every action, of both external or internal nature.
Firstly, the control application completely relieves security specialists from the need to compile dozens of written reporting logs. It is enough for the guard to enter a mark in the system, and the program itself takes into account the necessary action, comparing it with instructions, databases. The reports, without which control is impossible, are generated automatically, giving people the opportunity to devote time to their main professional activities.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-24
Video of control over security at the enterprise
This video is in Russian. We have not yet managed to make videos in other languages.
The control application records work shifts, shifts, the time of arrival and departure of the guard and employees, calculates the number of hours and shifts actually worked, keeps track of salaries, inventory records, and complete accurate financial reporting. And this is not a complete list of the capabilities of the powerful functionality of the program from our development team.
An advanced system for monitoring security activities at the enterprise in the basic version works in the Russian language. If you need to set up a different language, you should use the international version of the app, since the developers provide support for all countries and linguistic directions. The program is available for free download on the developer's website upon request. Within two weeks, the enterprise security service should be able to evaluate the capabilities in the demo version of the app. The full version is installed remotely, the developers connect to the company's computers remotely via the Internet, conduct a presentation and install the software. This saves time and hassle for both parties.
There are enterprises with special specifics of activities that require a different approach to safety and security issues. Their specificity differs from the traditional approach, and for such enterprises, USU Software can develop a personal version of the program for monitoring. In her work, all those nuances that are so important are provided.
Any enterprise, regardless of the profile of their production, large and small organizations, can use the software for monitoring security activities. The program will contribute to the correct automated security of shopping centers, hospitals, financial institutions. The system helps to establish control over the work of law enforcement agencies, law enforcement agencies, and also optimize the activities of private and departmental security companies. This security control system automatically generates databases and updates them constantly. Separate databases are formed by clients, partners, contractors, visitors, employees, and security guards. In addition to contact information, they contain a lot of other information, including the full history of the interaction of a person or company with an enterprise. For security purposes, it may be important to have scanned copies of documents, certificates, photographs of visitors and employees in the database.
The program can quickly, almost instantly process huge amounts of data in multi-user mode. It divides all information into convenient modules, categories. Comprehensive reporting and statistical data can be obtained for each group. The search bar and the usual query provide data on guard duty, by the number of visits, by employees, by the required dates, times, by a specific visitor or employee in seconds. This inspection program supports downloading files of any format and type without restrictions. This means that security instructions can be supplemented with room diagrams, three-dimensional models of the protected area, photographs, copies of documents, video recordings. It makes the work easier and also increases the degree of safety. If you put the composite images of criminals or persons on the wanted list in the system, then the program is able to recognize them at the entrance when trying to get to the enterprise, which the guard should find out about right away.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
USU Software automates the work of the checkpoint. If there are several checkpoints, it’ll unite them into single information space. It’ll be possible to create individual bar codes for employees, place them on badges or official IDs. The program reads codes and automatically enters all the data on the passage time of a particular employee. This way you can organize the monitoring of compliance with work discipline in order to see the time of arrival at work, leaving, unauthorized exits of each employee of the enterprise for any period.
The program shows what types of activities are more common in the security service at the enterprise. It can be escorting goods or working with visitors, guarding employees, premises, territory, patrolling. Based on this data, management is able to more accurately set tasks for the security service. The system facilitates control over every action of the guards. The manager sees in real-time where certain specialists are, what they are doing. At the end of the reporting period, the program generates a report on the personal effectiveness of each — it’ll show the number of hours worked and shifts, personal achievements. This information is useful in making decisions on promotion, dismissal, bonuses, payroll if the guard works on piece-rate terms.
The control program shows all the necessary data about any employee or guest, sorting the information by date, time, the purpose of the visit, and other criteria. Finding information does not take much time — you get the information you need in seconds. The system maintains complete financial statements, which are also useful for the head of the enterprise and the accounting department. The program also shows all the costs of ensuring the work of security, including even unforeseen ones. This helps to optimize costs when needed. Documents, reports, payment documentation using the program from our development team are configured automatically. Errors that are made by employees are completely excluded. Employees, including security, should be relieved of the need to keep paper records.
The program unites in one information space various departments, divisions, workshops of the enterprise, as well as checkpoints, security points. This enables the staff to communicate more quickly, to transfer information to each other without distortion and loss, and the manager should be able to ensure control over all spheres of the life of his organization.
This software has a convenient built-in scheduler, clearly oriented in time and space. With its help, managers should be able to plan any management activities, including the budget, the personnel department
Order a control over security at the enterprise
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Control over security at the enterprise
— to draw up a schedule, work schedules, and instructions, and each employee should be able to manage his time more rationally, clearly planning it. If something is missed or forgotten, the program should tactfully remind you of it.
The head of the enterprise must be able to customize the timing of receiving reports, statistics, analytical data at his discretion. They’ll also be able to receive data at any time when such a need arises. The monitoring program can be integrated with video cameras. Security officers receive comprehensive data in the captions of the video stream about the work of cash desks, warehouses, checkpoints. This should make observation easier. Software from our developers provides professional control over the state of warehouses. The system itself counts materials, raw materials, finished products, write off, as well as take into account the reception and transfer of special equipment, such as walkie-talkies, weapons by the guards, consider the availability of auto parts and remind of the need for purchases and the timing of maintenance.
The program can integrate with the enterprise website and telephony. This opens up amazing opportunities for doing business and building relationships with customers and partners. Also, the system can be integrated with any trade and warehouse equipment. Data on any action immediately goes to the statistics system. Access to the system is provided differentiated in order to avoid data leaks and information abuse. Each employee logs in under a login that opens to him the data of only those modules that are assigned to him according to the level of authority and competence. The security officer will not see the financial report, and the economist will not have access to the management of the enterprise entrance.
The control program can organize mass or personal distribution of information via SMS or e-mail.
Employees of the enterprise and regular customers should be able to get a specially developed mobile application. This system, despite the many possibilities, is very easy to use. It has an easy start, a simple interface, and an attractive design. It won’t be difficult for security guards, production workers, or managers to work in the control program, whatever the initial level of technical preparedness of the personnel.






