Operating system: Windows, Android, macOS
Group of programs: Business automation
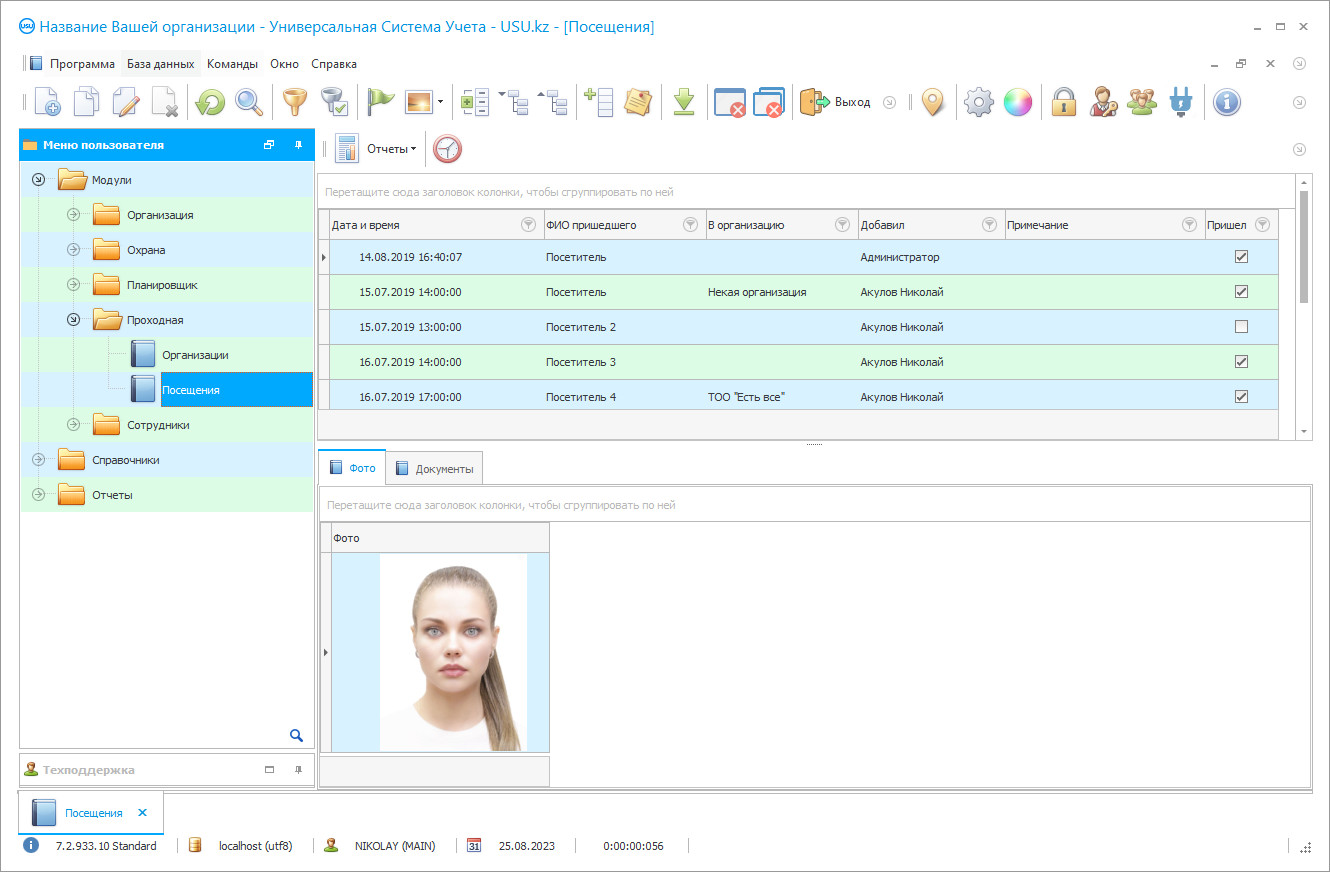
Program for control of security
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
The monitoring security program in modern conditions is a normal, widely used tool for managing the work of the security service. Such a program is used by both specialized security agencies that protect different customer's many objects, and commercial and government enterprises that prefer to create their own security units. Of course, systems of this kind can be very different from each other in structure, development and improvement possibilities, set of functions, number of restrictions, etc. Of course, if we consider ready-made solutions. Some companies with the appropriate financial capabilities order exclusive developments that take into account the most diverse nuances and details of activities. Accordingly, the cost of a ready-made program with different functionality can vary very seriously (not to mention individually developed program). The choice of the program should be approached with the utmost care and thoroughness. It is necessary to make sure that the program provides automation of all the main business processes related to security, the ability to embed various technical devices, processing, and storage of large amounts of information (including audio and video files), etc. In addition, when choosing a software program, you should keep in mind the company's development plans at least for the near future (so that you do not have to buy an extended version in two years due to the growth in the scale of the activity or active diversification).
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-23
Video of program for control of security
This video is in Russian. We have not yet managed to make videos in other languages.
USU Software system offers its version of a comprehensive accounting and management of security activities computer program. The USU Software security control program is developed at a professional level and meets the highest requirements of potential customers. All work processes and accounting procedures are automated in the program, there are no restrictions on the number of protected objects, integration of various technical devices is provided. The interface is simple and easy to learn even for a novice user. The modular structure of the program allows selecting the subsystems that are activated first. The electronic checkpoint ensures strict observance of the access regime established at the enterprise, control of the working time of employees (the personal pass scanner records the time of arrival and departure, late arrival, processing, etc.), registration of visitors by date, time, the purpose of the visit, duration of stay on the territory, the receiving employee or department, etc. Based on these data, summary reports can be generated for the company as a whole and individual employees, piecework wages and material incentives can be calculated, analytical reviews on the dynamics of visits, etc.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
Integration with the latest technologies and a wide range of technical devices (sensors, alarms, proximity tags, electronic locks, CCTV cameras, metal detectors, etc.) used in security, allows maximizing security measures and ensuring complete control without the need to expand the staff. Automatically generated control management reporting provides an opportunity to analyze and evaluate performance from various points of view, control and manage financial flows, make competent business decisions aimed at increasing profitability and strengthening the company's position in the market.
Order a program for control of security
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Program for control of security
The security control program from the USU Software is intended for use by specialized security agencies, as well as commercial and state enterprises that have their own security service. Setting the parameters of the control subsystems is carried out to each specific customer, taking into account the peculiarities of its functioning. The system is developed at the most modern level in full compliance with programming standards. The work processes and accounting procedures within the program are largely automated, which provides a noticeable increase in the level of enterprise security, on the one hand, and a decrease in operating costs, on the other.
USU Software provides effective control and accounting of the protection processes of an unlimited number of objects at the same time. Alarms from motion sensors, humidity and temperature sensors, fire and burglar alarms, video surveillance cameras, metal detector frames, and other equipment are sent to the central control panel of the duty shift. The built-in map (to each object under control) allows quickly tieing the signal to the terrain and sending the nearest patrol group to the scene. The electronic checkpoint provides reliable protection of the territory and strict access control. Thanks to the barcode scanner of a personal pass, the time of entry and exit of employees from the site, late arrival, processing, etc. are recorded. If necessary, a summary report can be prepared for all employees of the company or a sample for any employee. When registering visitors, the date, time, purpose of the visit, passport details of the guest, the receiving unit, etc. are recorded. One-time and permanent passes with the attachment of the guest's photo are printed right at the checkpoint. Analysis of the dynamics of visits can be carried out based on the accumulated statistics as needed. A set of automatically generated reports provides the company's management with up-to-date, reliable data on each object of protection separately, allows analyzing the results of work and making informed management decisions.
By an additional order, the program activates mobile customers and employees of the enterprise applications, integrates into the system of payment terminals, automatic telephone exchange, the application ‘The Bible of a Modern Leader’, etc.






