Operating system: Windows, Android, macOS
Group of programs: Business automation
Security organization system
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
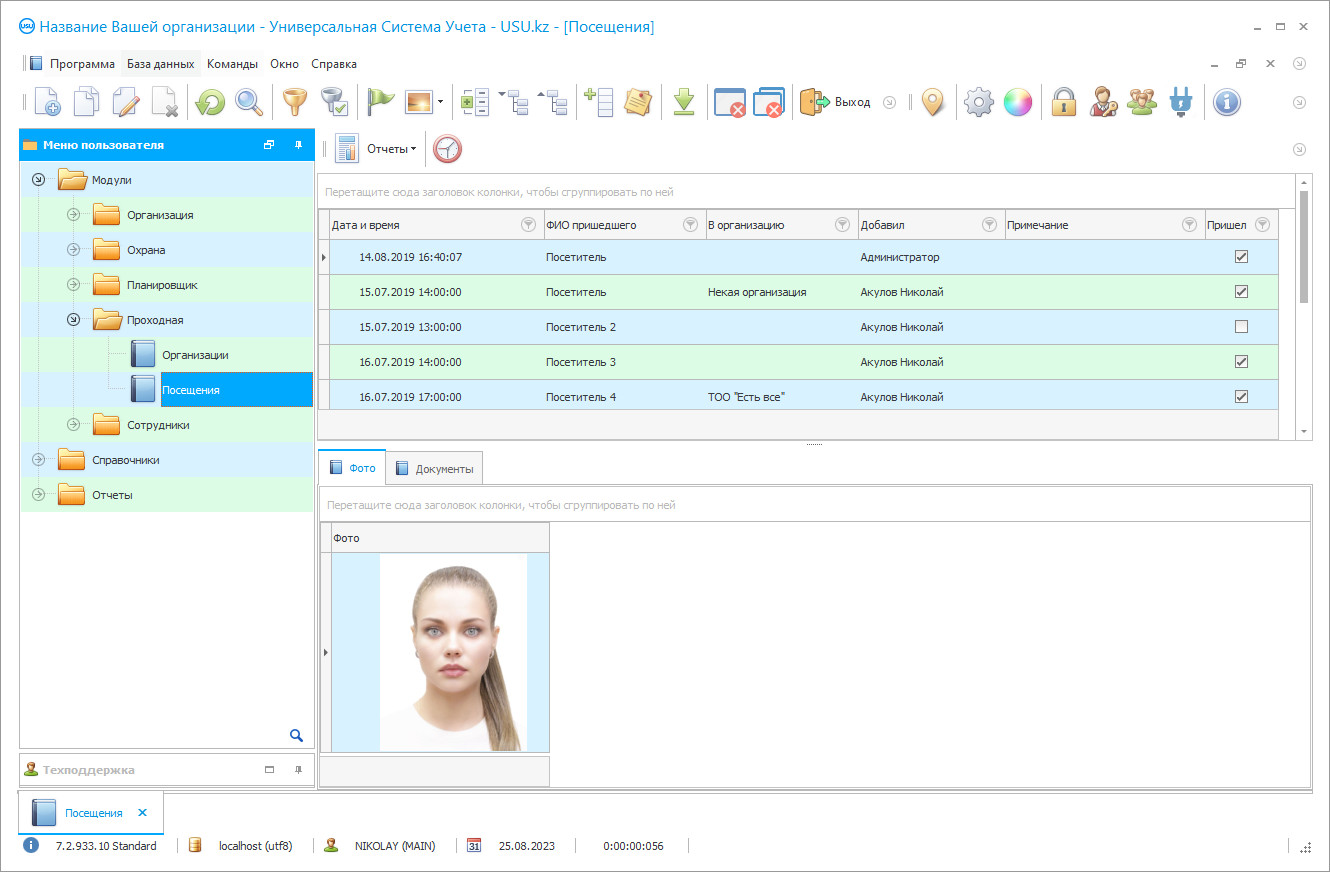
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
The security organization system is often underestimated by organization managers, and this poses a serious threat to the economic security of the organization. Everyone understands the need to protect their production, offices, intellectual and material property, and staff. They solve this problem in different ways. Some directors prefer to create their security service, others prefer to use the services of security firms. But whatever the decision, the leader must build a competent security system in his organization. As in most cases of management decisions, several important rules apply to the organization of security. The first says that it is not possible to achieve effective work without full-fledged planning. The second rule states that the fulfillment of the plan should be carried out not temporarily, but with constant systematic control with an analysis of all performance indicators. Control is needed both external and internal. External is the quality of security services, the efficiency, and completeness of the performance of all tasks assigned to security. Internal control is based on tracking all actions of personnel - security must work under instructions, rules established in the organization, in a disciplined manner.
Today, no one needs a nominal guard - pensioners sitting with books who do not have the professional skills necessary to ensure all the tasks assigned to the security service. Modern security guard requirements are more stringent. They must be able to protect the entrusted object and the people on it must understand the specifics of the organization to be able to advise visitors, direct them to the right specialist, to the right department. A well-built security system ensures that employees know how it works and where the alarm is installed, how to monitor the state of the panic button to call the police, how to handle weapons, ammunition, portable radios. A modern security guard must know perfectly how to carry out electronic access control, conduct an evacuation in case of an emergency, and provide first aid to victims. All these skills are indicators of the quality of the security service.
Internal control involves maintaining a large number of reports. They allow continuous tracking of actions and processes. Until recently, the security organization system was based on paper reports. Each guard kept a great variety of journals and accounting forms - recorded data on shifts and shifts, reception and transfer of radios and weapons, patrols and inspections, kept a record of visitors, carefully recording each in a journal, checked and recorded paper passes in the reports. In such a system, there are two significant drawbacks - a large amount of time spent on paperwork and low guarantees that the information is accurate, correct, and preserved for many years. Some are trying to ‘strengthen’ the organization of the security system with modern information technologies, making the guards the duty not only to write everything down but also to enter it into a computer. In this case, again, there are no guarantees of the safety and accuracy of the data, but the time spent on reporting work increases, and the effectiveness of professional activity decreases.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-23
Video of security organization system
This video is in Russian. We have not yet managed to make videos in other languages.
Neither method solves the main problem - the weakness of the human factor. The guard can get sick, forget to enter information, confuse something. Even the most honest and principled security officer can be intimidated, forced to violate instructions, not to mention corruption - if they want to ‘negotiate’ with the security, attackers usually succeed.
Security management cannot be made effective without addressing these problems. The ready-made version was offered by the USU Software system company. Specialists developed a security system organization. It can comprehensively solve all the main problems - automate document flow and reporting, saving employees from the need to fill out tons of paperwork and spend most of their working time on it, provide the manager with all the necessary reasonable planning and constant automatic control of each stage of activity tools, the quality of security and internal accounting, staff work. These capabilities allow you to fully organize a reliable and strong security system, in which the organization, its property, intellectual property, and employees out of danger.
The system automatically keeps track of shifts and shifts, monitor compliance with the established schedule of service, automatically make notes in the service sheets of guards, take into account the reception and transfer of special equipment, walkie-talkies. If we are talking about a security company, then the system itself calculates the cost of customer services, generates each area of activity reports. The system of security organization from USU Software can be safely entrusted with accounting and warehouse reporting. With its help, you can see the real state of affairs in the organization. The basic version of the system is in Russian. To work in other languages, you can use the international version. The developers provide all countries and language support. If there are some special specifics in the company's activities, you can tell the developers about it and get a personal version of the system developed specifically for the organization, which works taking into account specific data. The trial version can be downloaded free upon request on the developer's website. Within two weeks, you can add your idea of the functionality and capabilities of the system and decide to purchase the full version. It doesn't take time to install. A USU Software representative contacts you to connect to the organization computers remotely, conduct a presentation, and install the system.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
The system from USU Software contributes to the correct and competent organization of security at enterprises of various directions, in offices, shopping centers, hospitals, and other institutions. It helps to optimize and improve the work of law enforcement agencies and power structures, helps build an effective and accurate system of work in security agencies, enterprises, in any security service. The security structure organization system can work with the information of any volume and level of complexity. It divides the information flow into convenient categories, modules, for which it is then convenient to get all the information - reports, comparative and overview analysis, statistics. The system form convenient and useful databases - clients, customers, visitors, employees of the protected facility. For each person in the database, you can attach not only contact communication information, but also all information about the interaction, photos, data of identity cards. With the help of the organization system, it not difficult to fully automate the access control. The system conducts clear visual and digital control of entry and exit, entry-exit, export of goods, and import of raw materials. Each visitor automatically entered into the database, and the system certainly ‘recognize’ him at the next visit. The system can read data of electronic passes and barcodes on badges and IDs of employees. The manager is able to receive complete reporting information on all security services provided by the organization. The system shows which types of activities are in demand by clients most of all. The system display data on which services of partners the security organization itself uses most often. The system does not ‘hang’ or ‘slow down’, even if it contains a huge amount of data. It works instantly, in real-time. It is easy to find the necessary information in it in the search box by various criteria - by time, date, person, cargo, employee, the purpose of the visit, contract, object, income, expenses, and other performance indicators. The information is stored as long as required.
All documents, reports, contracts, and payment documentation are drawn up by the system automatically. People can devote more time to their main professional activities, constantly improving their qualifications and quality of services. Papers are no longer their ‘headache’.
Security software unites within a single information space various branches, posts, offices, different divisions, and departments of the organization, no matter how far from each other they are in fact. In this regard, employees begin to communicate more quickly within the framework of work, and the manager able to see the real state of affairs in each department. The program keeps records of personnel. Electronic access programs make it impossible to ‘negotiate’ with security. The system collects information about the time of arrival, a departure from work, an unauthorized departure from each employee workplace. The program shows the employment of each guard. At the end of the reporting period, the manager sees the personal effectiveness of any employee, his observance of labor discipline, and instructions. This can be important bonuses, dismissals, promotions information. The system keeps financial records and control, show income and expenses, adherence to the budget adopted in the organization. All this information helps accountants, managers, and auditors. The boss is able to set up automatic reports at a convenient frequency. If desired, you can receive reports once a day, once a month, or once a week. Report topics range from financial and economic to security benchmarks. The system provides warehouse accounting at an expert level. All changes in the use of weapons, fuels and lubricants, ammunition are taken into account, warehouses of materials, raw materials, finished products under control. The inventory takes place in a matter of minutes. If something comes to an end in the warehouse, the program shows it and offers to automatically form a purchase. You can load, save and transfer data to the program in any format - video files, photographs, diagrams, and three-dimensional models. Databases can be easily supplemented with scanned copies of documents, composite images of criminals. Integration of the system with video surveillance allows receiving text information in a video stream, which makes it easier to control cash registers, warehouses, checkpoints.
Order a security organization system
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Security organization system
The application honestly guards the safety of trade secrets. Each employee receives access to the system solely following their authority and position by personal login. The accountant never able to see information about the protected object, and the security officer not able to receive the financial statements of the organization. The backup function is configured at any frequency. The process of saving data does not require stopping the system, everything happens in the background. The system has a multi-user interface, the actions of one employee in it do not lead to internal conflicts with the simultaneous actions of another. The system can be integrated with the website and telephony. This opens up additional doing business and building unique relationships with the organization's customers opportunities.
In addition to software, employees can receive a specially developed mobile application. A leader can get an updated and expanded edition of the ‘Bible of the Modern Leader’, in which he will find many useful doing business and managing a control system tips.






