Operating system: Windows, Android, macOS
Group of programs: Business automation
Organization of work of security
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
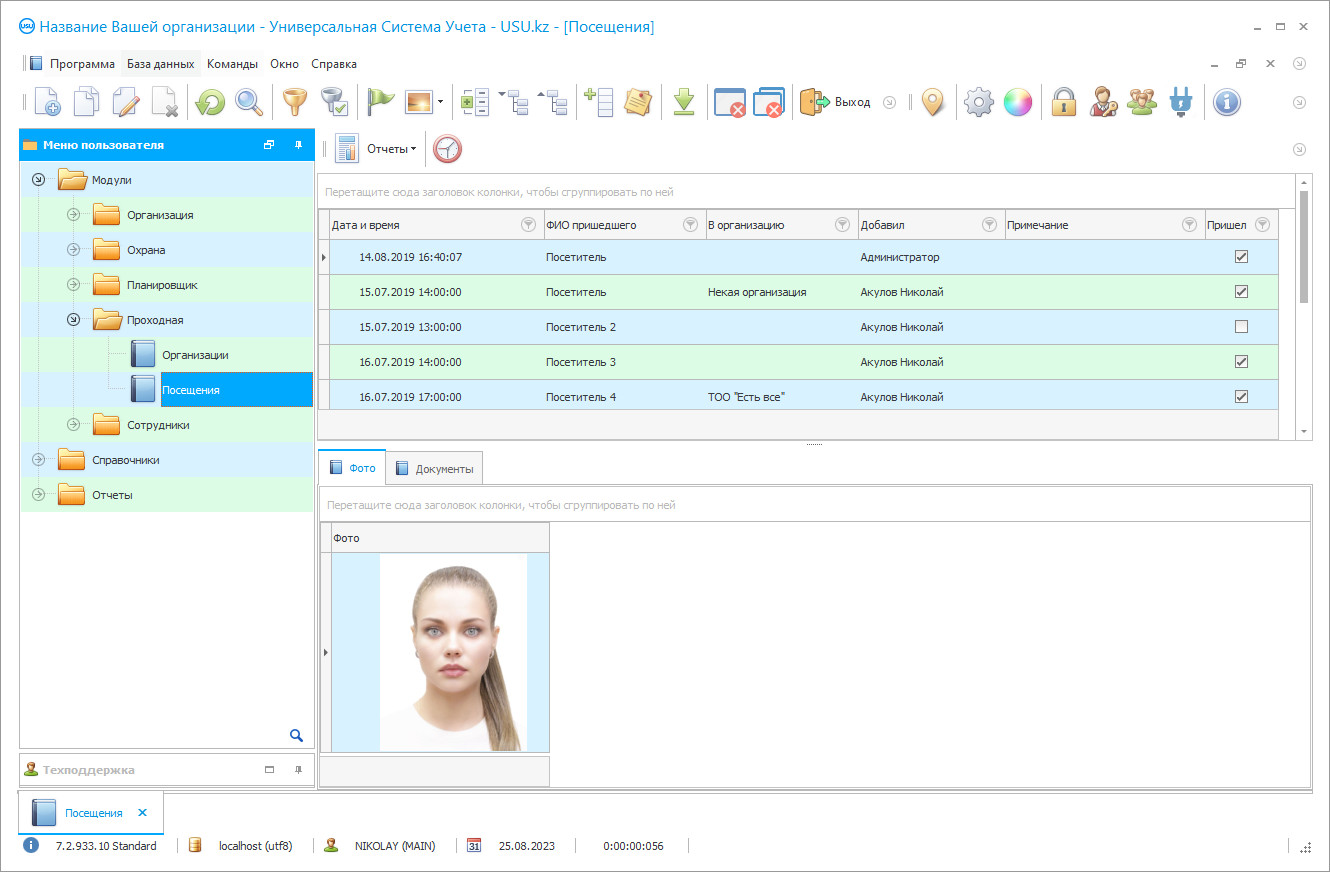
Organization of security work is an important issue for heads of security companies, security services, heads of companies in various fields of activity. Almost everyone turns to security services because safety is paramount in any business. Much depends on the correct organization of security activities, and therefore the desire to find tools and ways to do this effectively, quickly, and easily is quite understandable and natural.
The organization of the work of security services should take place with a clear understanding of what needs to be achieved in the end. It is important that the security guard does not sit out his shift from start to finish with a newspaper in his hands, but is able to meet the highest requirements of modern realities. He could protect the lives of other people at any time, ensure the safety of property and material values at a guarded facility, he could direct visitors to the right office or to the right specialist, since it is the security officer who first meets the client. A good security guard skillfully monitors the order and actions of everyone who comes to the organization, knows how the alarm works, and can, if necessary, carry out a quick evacuation and provide first aid to the injured.
But in order for security services to be of high quality, it is important not only to teach employees to apply all these skills in their work, to own a weapon, to be able to carry out detentions but also to ensure the correct accounting and control of all actions. For this purpose, the security is often charged with such a list of documentation, logbooks, and other paperwork that filling it out takes almost a full shift.
Security guards record data on the reception and delivery of duty, on the reception and delivery of special equipment, weapons, on quality checks of service, on visitors who came to the organization, on vehicles that entered its territory. The work of the security service won’t be effective if all these actions are performed by the old manual method, entering data into paper sources. The security guard can forget something, overlook something, fail to record or enter data with an error, the logs themselves can be damaged or lost. Organization of the work of a security organization using a combined method, in which manual maintenance is combined with duplication of information in a computer, requires even more effort and time, again without guarantees of information safety. The conclusion suggests itself — automation is needed, which will eliminate the influence of the human factor and reduce the likelihood of errors, while at the same time making work easier.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-23
Video of organization of work of security
This video is in Russian. We have not yet managed to make videos in other languages.
USU Software development team offers a simple and effective solution. Its specialists have developed software for organizing the work of security guards. The system helps to solve several important tasks at once, including a detailed analysis of the work of a security organization. The program saves staff from the need to devote most of their work to the preparation of papers and reports, and documentation. It’ll do all this automatically, and people will be able to engage in their main professional activities with a clear conscience, improving the quality of their activities.
The system from our developers takes into account work shifts and shifts, calculates wages, takes into account the availability of everything necessary for work in the warehouse, calculates the cost of services for customer companies, and provides statistical and analytical data on all areas of the security organization. The software will show what types of services are more in demand — the protection of goods, people, enterprises, installation and maintenance of alarms, escorting persons, etc. It’ll indicate the private expenses of the private security company, including unforeseen ones.
The basic version of the software works in the Russian language. The international version allows you to organize the work of protection in any language in the world, the developers pay special attention to the support of all countries. If a company provides services that differ from traditional ones, then there is an opportunity to get an individual version of the software, which is the best to take into account all the nuances and specifics of the work.
The program can be downloaded for free on the developer"s website. This will be a demo version that will allow you to evaluate the capabilities and powerful functionality of the software before deciding to purchase the full version. The system will help to carry out a competent and effective organization of the work of the security service at each enterprise, in the company, to improve the quality of work of a private security agency, and also to help organize the activities of various units in law enforcement and law enforcement organizations.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
The software for organizing security activities forms clear and functional databases of visitors, customers, contractors, customers, suppliers. For each of these categories, not only contact information is presented, but also the entire history of interaction. The database will show what services a particular client prefers, what his needs and requests are.
The system from the USU Software team helps to organize the access control, in which the control of visitors will be not only visual. Photos of visitors are saved in a special database, and it’ll be possible to find information about visits for any period. You can attach scanned copies of ID cards, passes to the pictures. The software for the organization of work displays all analytical and statistical information on the provided security services. It’ll also show what services the security service itself ordered and how much is spent on them. The data is stored for as long as required. The software helps, at the right time, on-demand, to carry out a quick search for any document, any history of a visit to the company, find data on each visitor, and set the goals of his visits.
This system unites different subdivisions and branches, security posts, and offices within a single information space. Their actual and geographical distance from each other does not matter. This helps to speed up the interaction of security personnel, ensure operational control over everyone. Organization and reporting for each department or post can be displayed in real-time. All documentation, reports, accounting, as well as contracts, payment documents, acts, forms, and certificates are generated automatically. This reduces the likelihood of errors and frees staff from the paperwork. The manager should be able to monitor all departments and each employee in real-time. The organization"s program will show where the security guard is, what he is doing, what his personal effectiveness and benefits to the company are.
An advanced software from the USU Software team conducts constant and error-free financial control, showing income, expenses, compliance with the budget. This information can be usefully used by accountants, auditors, managers. The program helps in organizing staff activities and improving the quality of services. You can put data on work schedules, plans into the system. It’ll show how much each security or security service specialist actually worked, what his achievements and successes are. This can be used to resolve personnel issues, award bonuses, and calculate payroll for piece rates.
Order an organization of work of security
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Organization of work of security
The system from USU Software helps the manager to set up the frequency of reports that they need. Automatically generated data on various information modules will be ready in due time — from a financial report to an assessment of the organization of personnel work, a report on the use of weapons, fuels and lubricants, ammunition. The required information in the form of tables, lists, graphs, and diagrams can be obtained not only within target dates but also at any convenient time.
You can load files of any format into the program. This means that security specialists receive not only written instructions, but also photographs, images of criminals, photographs of company employees who are allowed access, drawings and diagrams of the perimeters of guarded objects, schemes for installing alarms, and emergency exits, and video files. The latter is possible due to the integration of software with video cameras.
The organization"s system won’t allow compromising trade secrets or personal data. Access to the software is possible for employees only within the framework of their authority and competence. An individual password provides access only to certain information modules. In practice, this means that the driver of a security company will not be able to see financial reports, and a security guard won’t see management statistics, while an accountant won’t have access to customer data and facilities" features.
The backup function can be configured at any frequency. The process of storing information does not require stopping the operation of the system, and therefore this will not affect the activities of the guard. This software carries out a professional organization of warehouse accounting, calculates and divides into categories all equipment, overalls, ammunition, fuels and lubricants, auto parts, will take into account the timing and scope of technical inspection. When you use something, the write-off can be automatic, and the data will immediately go to statistics. If the required items run out, the system notifies you in advance and offers to form an automatic purchase.
The system can be integrated with the website and telephony. This should have a positive effect on the quality of services since customers will be able to see all the relevant information on the website of the security company and make an online order. When integrating with telephony, the program recognizes any customer from the database when they call. The employee will be able to pick up the
phone and immediately address the interlocutor by name and patronymic, which should pleasantly surprise the interlocutor. In the program, there is a possibility of operational communication at work by means of a dialog box. The organization will also benefit from the ability to install a specially developed mobile application on the gadgets of employees and regular customers.






