Operating system: Windows, Android, macOS
Group of programs: Business automation
Organization of security management
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
During business hours we usually respond within 1 minute
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
A screenshot is a photo of the software running. From it you can immediately understand what a CRM system looks like. We have implemented a window interface with support for UX/UI design. This means that the user interface is based on years of user experience. Each action is located exactly where it is most convenient to perform it. Thanks to such a competent approach, your work productivity will be maximum. Click on the small image to open the screenshot in full size.
If you buy a USU CRM system with a configuration of at least “Standard”, you will have a choice of designs from more than fifty templates. Each user of the software will have the opportunity to choose the design of the program to suit their taste. Every day of work should bring joy!
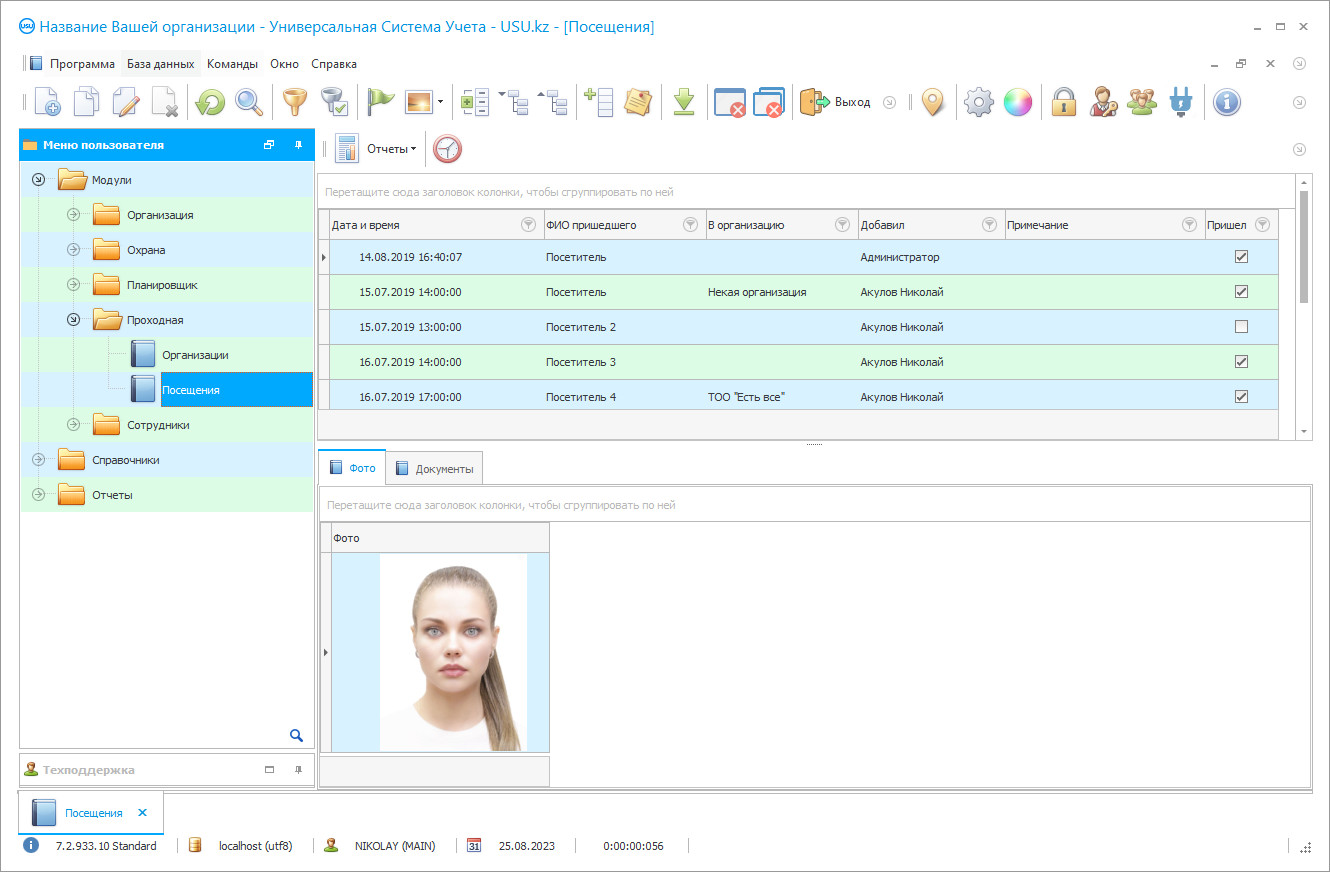
Organization of security management is a complex process that must be dealt with by the heads of protected objects and directors of security companies. The general principles of management in the field of security services correspond to the traditional principles of organization and management, but there are also some nuances. A great responsibility falls on the shoulders of the head — for their team and for the well-being of customers, clients of the security organization.
When organizing security management, it is important to remember that in this business, quantity creates only additional problems, but special attention should be paid to quality. In practice, this means that an overly bloated workforce is more likely to lead to confusion, confusion, and lack of oversight. A staff that is up to the task is easier to manage. For example, for the protection of an enterprise, if there is its own security service, one head of the security service is enough for five to nine guards, while the management of a security organization requires several departments and the delegation of control powers to their leaders.
The management system of a security organization can be built differently when the head is directly involved in the control of each stage of activity, but this is rather a rarity. No matter how the management process was initially built, it’ll be effective only if two indispensable conditions are met. The first is strict internal control, management of the personnel of a security organization or its own production security service. The second condition is constant monitoring of all indicators of the quality of activities. It will be possible with a clear conscience to entrust the security with any complex tasks only when each of its employees will, on the one hand, feel their own importance for the team, and on the other hand, understand that each of his actions is under control.
It is equally important to pay attention to planning when organizing management. Only if the security team and the leader know exactly what goal they are moving towards, the goal becomes real and accessible. In a security company and in the security service of a particular company, there are certain difficulties that impede perfect and accurate management and control. This is the inconstancy of the team, because most of the employees work in shifts, the need to relocate specific people to new objects, a new scope of work.
But ideally, you need to strive for a clear system in which subordination exists, rules and instructions are followed. Creating a friendly and efficient team in a security company is already half of the success. And this will also be facilitated by continuous analysis of performance indicators. On its basis, for example, it is possible to select partners for the guards who match the psychological and social type as closely as possible. This will help in increasing the motivation of employees, create a spirit of competition. A correct analysis of the activities of the team helps to build a competent reward system. Management will become easier if there is a discipline in the security organization or the security service of the enterprise.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-11-23
Video of organization of security management
This video is in Russian. We have not yet managed to make videos in other languages.
It can be achieved if each security officer clearly knows his duties and is aware of the consequences of their violation, if the management conducts control not from time to time, depending on the mood, but constantly, systematically. Understanding these rules makes it obvious a simple truth — security management without control is not possible. You can control the work of the security service in different ways. For example, it couldn't be easier to get employees to write tons of paper reports for every action they take. In this case, the staff will keep logs of records of duties, shifts, objects, delivery, and reception of radio stations and weapons, registration of visitors at a guarded facility, accounting of the work of checkpoints and checkpoints, vehicle entry and exit, inspection of the panic button for an emergency call of the police, and so on. There is no doubt that the guards spend most of their working time on writing.
You can optionally save the written report data to a computer. And in this case, the working day will not be enough, and a gap will appear in professional activity since the guards simply won’t have time for the main duties. Maintaining the quality of security services at a high level is possible only by freeing people from the need to keep a constantly written report. This can be achieved by automating reporting.
Such a simple and functional solution was offered by USU Software. Its specialists have developed software for managing security and security companies. The program transfers all document flow and reporting to an automatic level, freeing up time for employees to perform their duties with maximum quality. The software from our development team gives the manager a unique planning tool, helps in the organization of continuous systematic monitoring of all performance indicators. But the most important thing is that the system from our developers minimizes the influence of the human factor. If an offender can negotiate with a security guard, intimidate him, force him to violate instructions, then an impartial system will neither convince nor frighten him. The security will always be reliable.
The software from our team independently takes into account shifts and shifts count the amount of time worked by each employee, calculates his salary if the specialist works on piece-rate terms. Our program can create and update incredibly functional and convenient databases, automatically generate all documents — from contracts to payment documents. The system provides the manager with detailed reports on each area of the private security company.
This program can show which types of services from the list provided by the organization are most in-demand, and this helps to correctly plan activities in strong and weak directions. The program can automate the activities of checkpoints and checkpoints, conduct automatic control of passes, making it as easy as possible for service activities. An advanced system will keep full financial records, warehouse reporting at an expert level.
Download demo version
When starting the program, you can select the language.
You can download the demo version for free. And work in the program for two weeks. Some information has already been included there for clarity.
Who is the translator?

Khoilo Roman
Chief programmer who took part in the translation of this software into different languages.
The basic version of the security management software works in Russian. To configure it to work in a different language, you should choose the international version. Developers collaborate with all countries and linguistic areas. The trial version can be downloaded free of charge on our official website. After two weeks, you can make an informed decision about installing the full version. Installation is quick and remote. A company representative simply connects remotely via the Internet to the customer's computers, conducts a presentation of the software capabilities and installs.
If the work of the security service team or security company has some nuances that differ from traditional ones, you can inform the developers about this, and personal software will be developed for your security, which is an ideal option for this particular organization.
The management organization system from the USU Software team generates databases for any categories. For example, a separate database of customers of a security organization will be formed, in which, in addition to contact information, the entire history of interaction, requests, orders, and features of cooperation will be displayed. Separately, a database of employees of the guarded facility will be formed to fully automate the access control. A separate database of partners, suppliers, contractors will be created. The software can work with information in any volume. The system divides large and messy data into clear and simple modules, categories, groups. And for each of them, you can get any statistics, analytical, and reporting data for any period. For example, by monitoring visitors, employees, by the volume of orders for security services, by date, time, by the income or expenses of the organization.
The security management system supports loading and saving files of any format. This greatly facilitates the work and makes it possible to promptly exchange the necessary information. For example, you can add files with a description of an object, alarm schemes, photographs of employees, visitors to any customer — the program identifies everything and everyone. If you put pictures of wanted criminals in the database, the software will recognize them if they try to get into the protected areas.
The program can conduct full-fledged face control, comparing face images with databases, and can also read electronic passes, bar codes from IDs and passes. The system does not make mistakes, it is impossible to negotiate with it, and therefore the head of the protected facility should be able to get real information about when the employees of his organization come to work, leave it — the program immediately sends all data on actions with passes to statistics.
Order an organization of security management
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

Send details for the contract
We enter into an agreement with each client. The contract is your guarantee that you will receive exactly what you require. Therefore, first you need to send us the details of a legal entity or individual. This usually takes no more than 5 minutes

Make an advance payment
After sending you scanned copies of the contract and invoice for payment, an advance payment is required. Please note that before installing the CRM system, it is enough to pay not the full amount, but only a part. Various payment methods are supported. Approximately 15 minutes

The program will be installed
After this, a specific installation date and time will be agreed upon with you. This usually happens on the same or the next day after the paperwork is completed. Immediately after installing the CRM system, you can ask for training for your employee. If the program is purchased for 1 user, it will take no more than 1 hour

Enjoy the result
Enjoy the result endlessly :) What is especially pleasing is not only the quality with which the software has been developed to automate everyday work, but also the lack of dependency in the form of a monthly subscription fee. After all, you will only pay once for the program.
Buy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Organization of security management
An advanced control system maintains full internal control over the security service. Show statistics for each guard — how much he worked, when he came and left, at which facility he was on duty on certain dates. In real-time, the manager will be able to see the employment of the security service and its load. At the end of the reporting period, the manager sees not only a report on the work of the team as a whole but also indicators of the personal effectiveness of each. This can be used for the system of rewards, bonuses, punishments and for making the necessary personnel decisions.
The software provides detailed financial statements. Shows all the income and expenses of the organization, displays its own operating expenses. This data can be used by an accountant and an auditor, and also be useful to the head for making management decisions. The safety of information should not be in doubt. Any data, documents,
statistics, instructions, contracts, or payment documents will be stored for as long as needed. The backup is carried out periodically, it can be configured arbitrarily. The copying process itself does not require a temporary stop of the program, everything happens in the background, without prejudice to the work of the organization.
This program is distinguished by its high performance and speed. No matter how large the data loaded into it, finding the information you need takes only a few seconds. You can set any search category — by date, time, employee, service, customer, and a host of other indicators. The system unites different branches, security posts, offices of the organization within a single information space. Employees get the opportunity to interact more efficiently in the course of work, and the manager can see the real state of affairs in the current time mode for each post or branch. The software has a built-in scheduler that will help the manager to carry out competent management With its help, you can create a budget and carry out long-term planning, make work schedules for staff. Each employee of the organization with the help of the planner will be able to manage their working time more rationally, without forgetting about anything important.
The manager can set up reports with the frequency and frequency that is convenient for them — every day, every week, month, year. If you need to get data outside the schedule, this can be easily done at any minute. The reports themselves will be presented in the form of graphs, charts, and tables with comparative data for the past period. Our program integrates with video cameras, providing more detailed control over objects, including control over the work of security personnel. Employees receive access to the system according to their position and authority. This ensures the safety and security of information. The security guard cannot see financial reports, and the accountant cannot connect to customer databases and access descriptions of protected objects. The management program maintains an expert warehouse inventory of the security company, showing the availability of the necessary and informing that the necessary for the activity is coming to an end. An advanced control system helps to organize mass and personal distribution of information via SMS or e-mail integrates with telephony and the organization's website.






